
No more Custom Policies & Identity Experience Framework
With the new Entra External ID and Entra ID, we can use the built-in policies for authentication.
Entra External ID technical details and requirements:
- authentication method must be supported by the tenant; no custom authentication methods
- via user flow, we can select a password or OTP (one-time password) method.
- no custom methods like magic link or passwordless (yet!)
- no ADMIN API to authenticate users;
- no API connector to use external API for authentication;
Compare User with password and OTP
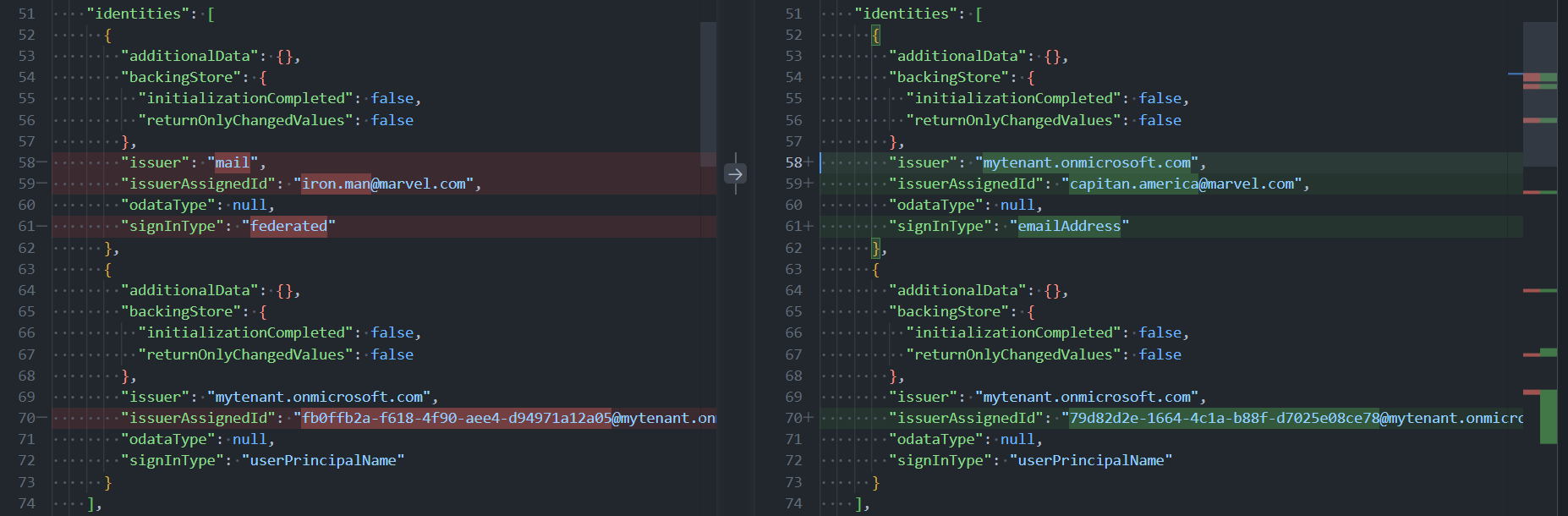
User with password
{
"identities": [
{
"additionalData": {},
"backingStore": {
"initializationCompleted": false,
"returnOnlyChangedValues": false
},
"issuer": "mytenant.onmicrosoft.com",
"issuerAssignedId": "[email protected]",
"odataType": null,
"signInType": "emailAddress"
},
{
"additionalData": {},
"backingStore": {
"initializationCompleted": false,
"returnOnlyChangedValues": false
},
"issuer": "mytenant.onmicrosoft.com",
"issuerAssignedId": "[email protected]",
"odataType": null,
"signInType": "userPrincipalName"
}
]
}
User with OTP
{
"identities": [
{
"additionalData": {},
"backingStore": {
"initializationCompleted": false,
"returnOnlyChangedValues": false
},
"issuer": "mail",
"issuerAssignedId": "[email protected]",
"odataType": null,
"signInType": "federated"
},
{
"additionalData": {},
"backingStore": {
"initializationCompleted": false,
"returnOnlyChangedValues": false
},
"issuer": "mytenant.onmicrosoft.com",
"issuerAssignedId": "[email protected]",
"odataType": null,
"signInType": "userPrincipalName"
}
],
}
Differences & details
- signInType:
emailAddressfor the user with password,federatedfor the user with OTP - issuer:
mytenant.onmicrosoft.comfor the user with password,mailfor the user with OTP
Passwod + OTP?
Can we have a user with both a password and OTP? Yes, but there is in my opinion one issue. Look at the case.
Setup for demonstration:
- Two ‘User flows’ - first with password, second with OTP.
- Two Applications - there is a
one to manyrelation: user flow to application. One flow can have many applications, but one app can have only one user flow. - Create a user with a password. Via Graph API, we can update the user
identitiesand add an OTP authentication method. - With the Password and OTP user flow, we can test sign-in with both methods.
Issue and Limitation: The OTP authentication method is a ‘federated’ type, it gets the priority 0 (counting as in normal programming languages array from 0). Running the user flow with password and OTP we are always asked for OTP.
^ ⚠️ A user flow can’t force the user to use password based on the user flow authentication method.
What next?
We can build a component to change the authentication method from password to OTP via the profile page or application.
Passwordless
Now the OTP is threated as ‘federation’, but what will be for passwordless? With Graph API based on the Entra ID (and workforce tenant) we can check identities for federation and authentication/methods (for user like `https://graph.microsoft.com/v1.0/users/e{{user-object-id}}/authentication/methods)
^ ⚠️ Passwordless is not implemented yet!! ⚠️
Example from Entra ID - Workforce tenant
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#users('e33d2153-2c9b-4a45-834a-12af7e60aa29')/authentication/methods",
"@microsoft.graph.tips": "Use $select to choose only the properties your app needs, as this can lead to performance improvements. For example: GET users('<guid>')/authentication/methods?$select=id",
"value": [
{
"@odata.type": "#microsoft.graph.passwordAuthenticationMethod",
"id": "18c10230-6103-485e-b985-444c60001410",
"password": null,
"createdDateTime": "2024-07-04T11:32:09Z"
},
{
"@odata.type": "#microsoft.graph.phoneAuthenticationMethod",
"id": "3179e48a-750b-4051-897c-87b9720928f7",
"phoneNumber": "+48 6005006001",
"phoneType": "mobile",
"smsSignInState": "notAllowedByPolicy"
},
{
"@odata.type": "#microsoft.graph.fido2AuthenticationMethod",
"id": "25JaSCRw30ybzntTIr7m_QxVccdeMYAHixbwA2KlHAopdWb57vMomAtgmKEWcy-i0",
"displayName": "USB-A - yubikey - green",
"createdDateTime": "2023-12-08T18:38:00Z",
"aaGuid": "2ff0579a-8113-47ba-b226-bb5a8db9202f",
"model": "YubiKey 5 Series with NFC",
"attestationCertificates": [
"2392ea7fe8e1ecfc7164ffb85170bd0978b36ad1"
],
"attestationLevel": "attested"
},
{
"@odata.type": "#microsoft.graph.fido2AuthenticationMethod",
"id": "J4knu4Z86pdSt_AfWjPyWrq1sVblUpljGiabaeLNMMHMl_-q7kDF6k3HR7_SxPY50",
"displayName": "USB-A - yubikey - black",
"createdDateTime": "2022-11-30T08:23:42Z",
"aaGuid": "2fc0579f-8113-47ea-b116-bb5a8db9202a",
"model": "YubiKey 5 Series with NFC",
"attestationCertificates": [
"2392ea7fe8e1ecfc7164ffb85170bd0978b36ad1"
],
"attestationLevel": "attested"
},
{
"@odata.type": "#microsoft.graph.microsoftAuthenticatorAuthenticationMethod",
"id": "b5c69aef-4cfe-4fef-affe-6b1b39d4cb69",
"displayName": "GooglePixel 9 Pro",
"deviceTag": "Android",
"phoneAppVersion": "6.2504.2323",
"createdDateTime": "2024-07-30T12:43:26Z"
}
]
}
What we can see:
- Nice and clear information from @odata.type about the method like fido2 or authenticator app.
- All details with displayName.
- Audit with createdDateTime.
Summary
- If the Entra External ID team relies on the Workforce authentication methods, we will use authentication methods to check the current user setup for password and passwordless methods and identities for OTP and federations.
- With GraphAPI we can manipulate and change authentication methods and add/remove federations.