Updated: 30-06-2024
Playground
Entra Verified ID Workshop
Do you want to try it?
Use my GitHub repository to set up your credentials. Entra Verified ID Workshop
You can start with my workshop and create a simple flow with Entra Verified ID. All divided into steps with the code and the explanation.
Big Picture
Verifiable Credentials solve problems for identities in the digital world. What does it mean? Please check the story: You own the national ID card. It is in your wallet. To get the document, you must visit the government office, provide information/documents, check your identity with your old ID, passport, or proof of birth, and wait for the document.
Details:
- The government issues the document. It is accepted by the European Union and in other countries.
- Your photo, name, identification number, and document identification number are there.
- You can use it to prove your age, nationality, and verify identity.
Can we do the same in the metaverse? I don’t know, but I know that you can use Verifiable Credentials to build your identity in the digital world. In November 2019, W3C published the first version of Verifiable Credentials. The specification is available here. The commit with the document on GitHub.
Is the flow/architecture different from the National ID card? In my opinion, it is similar. When we move to the digital world, we have even more options.
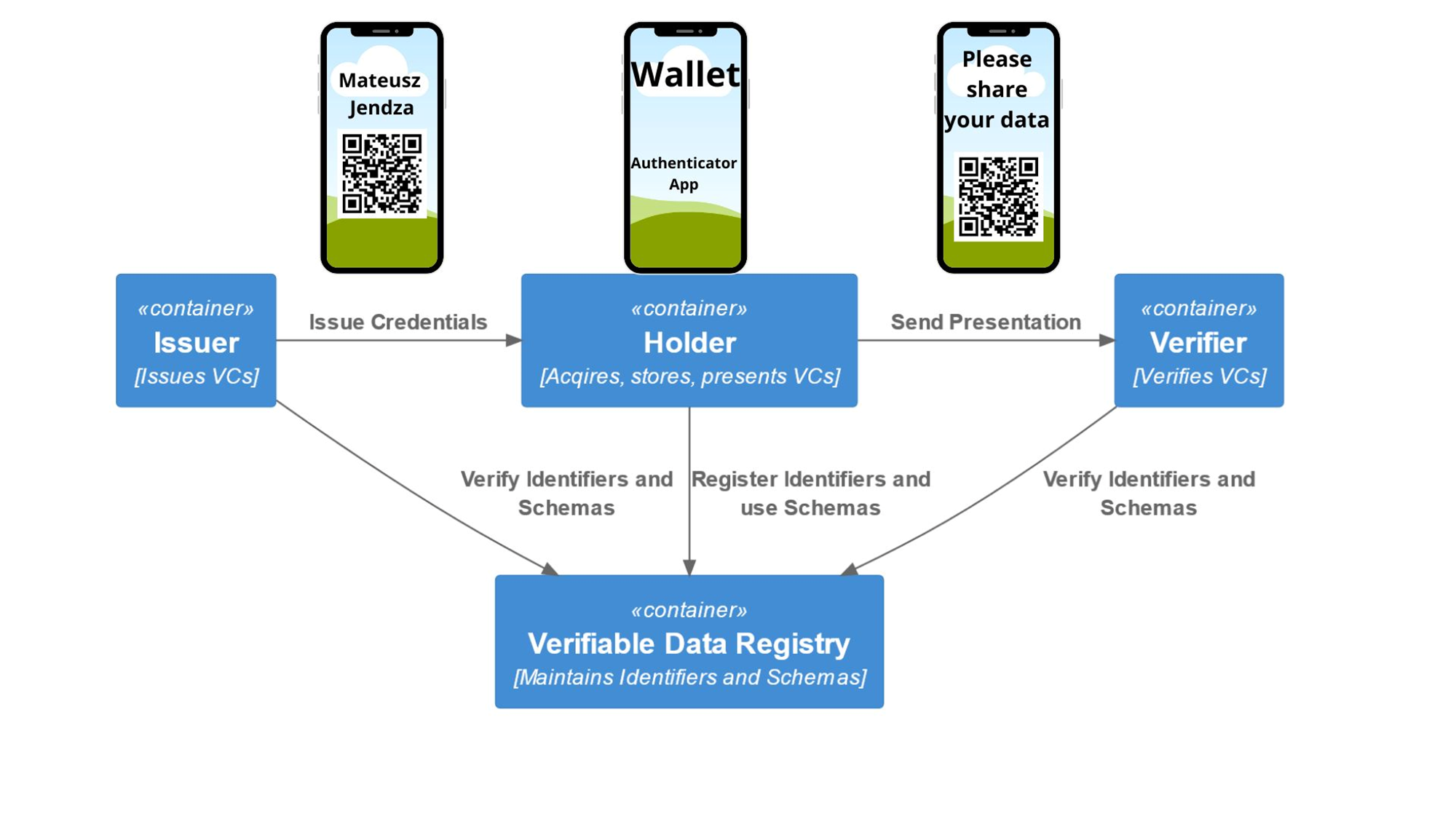 Entities in the system:
Entities in the system:
- Issuer - can be a government, a bank, or a company/organization. Do you manage your organization via Entra ID? You can use Entra Verified ID to issue Verifiable Credentials. The entity asserts claims about the subject.
- Holder — in the real world, you keep the document in your wallet. In the digital world, you need a Verifiable Credential in your digital wallet. To start the journey, you can use the Microsoft Authenticator App. Do you need more? Build your own with SDK.
- Verifier - can be a government, a bank, or a company/organization. The entity asks for the VC presentation, or in the zero-knowledge proof, that the entity verifies the claim without seeing the data.
Is it secure?
We protect data based on PKI (Public Key Infrastructure). The Verifiable Data Registry is a public place where we can check the public key for the Issuer. The Holder can publish the DID Document to the Blockchain. The Verifier can verify the public key for the Holder. So, answering the question: yes, it is secure.
Issuer
From the issuer’s perspective, with the DID (Decentralized Identifier) published to the web (DID Document), we can check the public key in the manifest deployed to the web manifest.
issuer did document
{
"id": "did:web:verified-id.factorlabs.pl",
"@context": [
"https://www.w3.org/ns/did/v1",
{
"@base": "did:web:verified-id.factorlabs.pl"
}
],
"service": [
{
"id": "#linkeddomains",
"type": "LinkedDomains",
"serviceEndpoint": {
"origins": [
"https://verified-id.factorlabs.pl/"
]
}
},
{
"id": "#hub",
"type": "IdentityHub",
"serviceEndpoint": {
"instances": [
"https://hub.did.msidentity.com/v1.0/6790fadf-9751-4f73-8f65-844675b9a22a"
]
}
}
],
"verificationMethod": [
{
"id": "#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9",
"controller": "did:web:verified-id.factorlabs.pl",
"type": "EcdsaSecp256k1VerificationKey2019",
"publicKeyJwk": {
"crv": "secp256k1",
"kty": "EC",
"x": "TWwp5A43z2vjmndG9-AGsqYU8lCLZApQbOFbEz4_rIE",
"y": "MpOKpoOUfrIdLXxABlOD03DI0SwvrsnqUpNb5P7Pxak"
}
}
],
"authentication": [
"#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9"
],
"assertionMethod": [
"#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9"
]
}
Holder
It is more complex for the holder - you, as a ‘person’ don’t have a standard public internet address/space. But with help from the Blockchain, we can solve this problem. The holder publishes the DID Document to the Blockchain. Please find your DID Document on the ION Blockchain with my demos (scroll down the article): for example, one of my DIDs is here
holder did document
{
"@context": "https://w3id.org/did-resolution/v1",
"didDocument": {
"id": "did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsImt0eSI6IkVDIiwidXNlIjoic2lnIiwieCI6IlNRS2V0aFdnQWtocGNnaUR3czBaTXJDa2k5TzFIRVMtVmVhUTdmeFhSSU0iLCJ5IjoiUEZSTDZnNDROU0pXanlLQnlkRVZ2T1JDMm9qODV3bVFhR1B3bW1GREpYcyJ9LCJwdXJwb3NlcyI6WyJhdXRoZW50aWNhdGlvbiJdLCJ0eXBlIjoiRWNkc2FTZWNwMjU2azFWZXJpZmljYXRpb25LZXkyMDE5In1dfX1dLCJ1cGRhdGVDb21taXRtZW50IjoiRWlEYlR2ZG5sajBqdEJJcm9iNEJ2MVVMRnJJU0xnSkxyM3c2MHBENElYcWFxdyJ9LCJzdWZmaXhEYXRhIjp7ImRlbHRhSGFzaCI6IkVpRGRLSXdWdzNfZ2QtaWplNTVuLXdWQ3psczNwZUxITXVUczBPcU50blp2MFEiLCJyZWNvdmVyeUNvbW1pdG1lbnQiOiJFaUM1Y0FsaHlLRWNDejhzYWJidDVwLWpWSzNRSmt2cVdFVFQ5c0J5U2ctcW9nIn19",
"@context": [
"https://www.w3.org/ns/did/v1",
{
"@base": "did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsImt0eSI6IkVDIiwidXNlIjoic2lnIiwieCI6IlNRS2V0aFdnQWtocGNnaUR3czBaTXJDa2k5TzFIRVMtVmVhUTdmeFhSSU0iLCJ5IjoiUEZSTDZnNDROU0pXanlLQnlkRVZ2T1JDMm9qODV3bVFhR1B3bW1GREpYcyJ9LCJwdXJwb3NlcyI6WyJhdXRoZW50aWNhdGlvbiJdLCJ0eXBlIjoiRWNkc2FTZWNwMjU2azFWZXJpZmljYXRpb25LZXkyMDE5In1dfX1dLCJ1cGRhdGVDb21taXRtZW50IjoiRWlEYlR2ZG5sajBqdEJJcm9iNEJ2MVVMRnJJU0xnSkxyM3c2MHBENElYcWFxdyJ9LCJzdWZmaXhEYXRhIjp7ImRlbHRhSGFzaCI6IkVpRGRLSXdWdzNfZ2QtaWplNTVuLXdWQ3psczNwZUxITXVUczBPcU50blp2MFEiLCJyZWNvdmVyeUNvbW1pdG1lbnQiOiJFaUM1Y0FsaHlLRWNDejhzYWJidDVwLWpWSzNRSmt2cVdFVFQ5c0J5U2ctcW9nIn19"
}
],
"verificationMethod": [
{
"id": "#ba6bddbe642d439c96b15ea72ed5a887",
"controller": "did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsImt0eSI6IkVDIiwidXNlIjoic2lnIiwieCI6IlNRS2V0aFdnQWtocGNnaUR3czBaTXJDa2k5TzFIRVMtVmVhUTdmeFhSSU0iLCJ5IjoiUEZSTDZnNDROU0pXanlLQnlkRVZ2T1JDMm9qODV3bVFhR1B3bW1GREpYcyJ9LCJwdXJwb3NlcyI6WyJhdXRoZW50aWNhdGlvbiJdLCJ0eXBlIjoiRWNkc2FTZWNwMjU2azFWZXJpZmljYXRpb25LZXkyMDE5In1dfX1dLCJ1cGRhdGVDb21taXRtZW50IjoiRWlEYlR2ZG5sajBqdEJJcm9iNEJ2MVVMRnJJU0xnSkxyM3c2MHBENElYcWFxdyJ9LCJzdWZmaXhEYXRhIjp7ImRlbHRhSGFzaCI6IkVpRGRLSXdWdzNfZ2QtaWplNTVuLXdWQ3psczNwZUxITXVUczBPcU50blp2MFEiLCJyZWNvdmVyeUNvbW1pdG1lbnQiOiJFaUM1Y0FsaHlLRWNDejhzYWJidDVwLWpWSzNRSmt2cVdFVFQ5c0J5U2ctcW9nIn19",
"type": "EcdsaSecp256k1VerificationKey2019",
"publicKeyJwk": {
"crv": "secp256k1",
"kid": "ba6bddbe642d439c96b15ea72ed5a887",
"kty": "EC",
"use": "sig",
"x": "SQKethWgAkhpcgiDws0ZMrCki9O1HES-VeaQ7fxXRIM",
"y": "PFRL6g44NSJWjyKBydEVvORC2oj85wmQaGPwmmFDJXs"
}
}
],
"authentication": [
"#ba6bddbe642d439c96b15ea72ed5a887"
]
},
"didDocumentMetadata": {
"method": {
"published": false,
"recoveryCommitment": "EiC5cAlhyKEcCz8sabbt5p-jVK3QJkvqWETT9sBySg-qog",
"updateCommitment": "EiDbTvdnlj0jtBIrob4Bv1ULFrISLgJLr3w60pD4IXqaqw"
},
"equivalentId": [
"did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w"
]
}
}
Scenarios
I created a demo page where you can test different Verifiable Credentials with Entra Verified ID: DEMO links https://vc.factorlabs.pl.
Verified Employee
Specification:
- Based on your organization identity (ID token), you can issue a Verifiable Credential for you as the employee.
- You can use my page with the QR Code to test the verified employee flow
- My version requires signing in to the Organization with Entra ID to generate the Employee Verified ID.
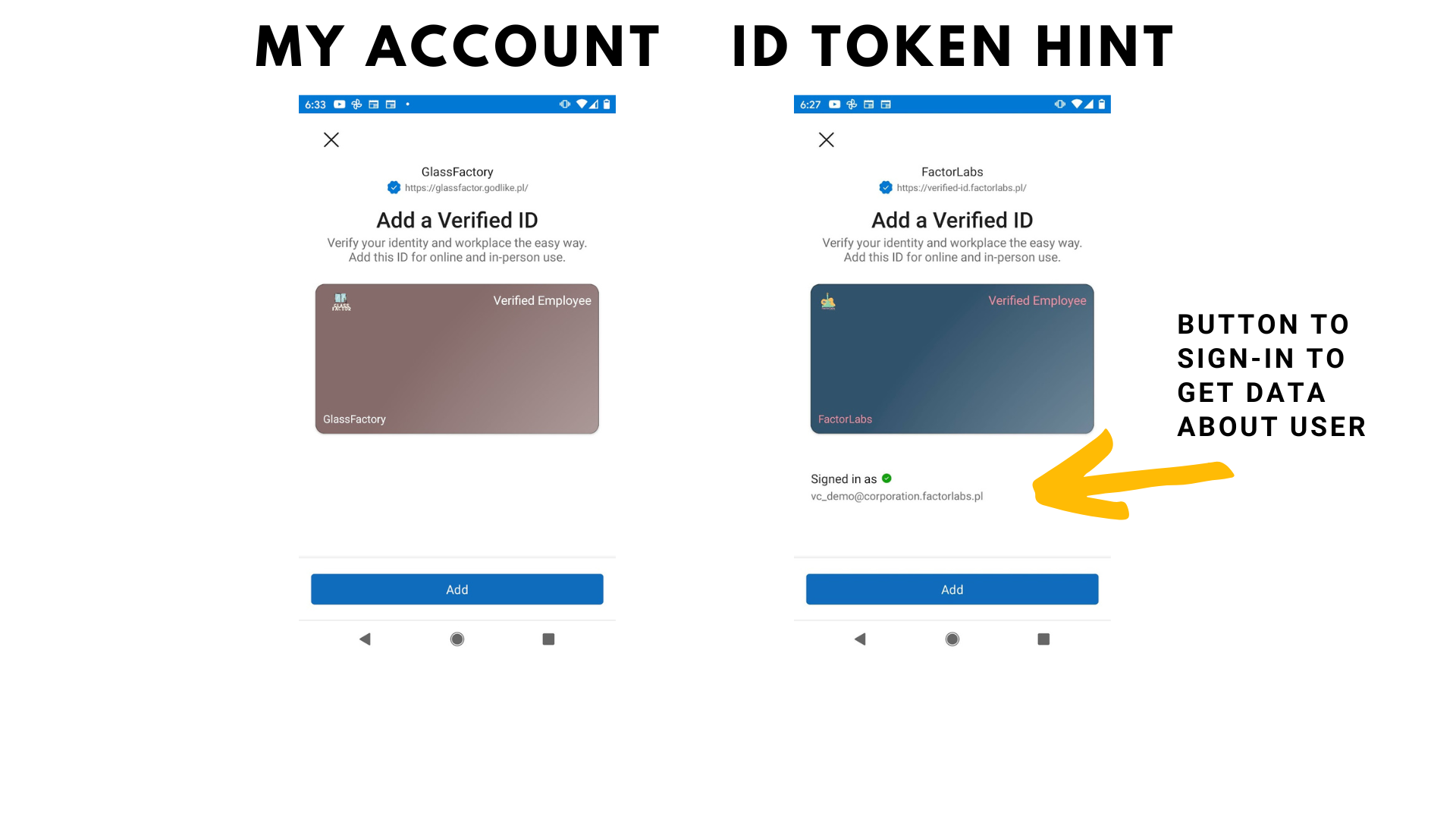
You can use Microsoft Entra ID page called My Account. To run/test the flow - you must enable Entra Verified ID. With the My Account page - all data about the user is delivered from the account - without a wallet sign-in (“ID token hint”). To use Face Check you need to add a picture to your account.
Are you an Entra ID admin?
You can enable Entra Verified ID for your organization.
My presentation with the presentation page.
Is your account with a picture? You can use Face Check with the presentation page VC presentation with Face Check - the process uses the jpg image stored in the VC Claim - not from the account.
Please check the picutre below - left side is issuance process from My Account and right side is via custom page and token hint.
Use VC as a passkey for Azure AD B2C

A while ago, I started my journey with VC. I decided to test it - my first idea was to use it to design and develop password-less B2C sign-up/sign-in flows for Azure AD B2C.
Please check my demo Portal Factorlabs - the page is available here.
Specification:
- Azure AD B2C integration
- Password-less sign-up/sign-in
- One full flow - sign in as the first step, then sign up with VC, and as the final step ‘sign in with VC’ (without caning screens/flows)
- No user data at all - don’t have email, phone
- You can build a similar flow selling your product - generate VC from a link in the email, product guide, or a basic website with the ‘device id’ field - like my demo for Products and Ingredients - Issue Ingredient VC card.
Business scenario:
You can get the account/access only via invitation - we can invite you to the system/application and use VC as the passkey to authenticate the user in the ecosystem.
The demo page - you can check details about the presented VC
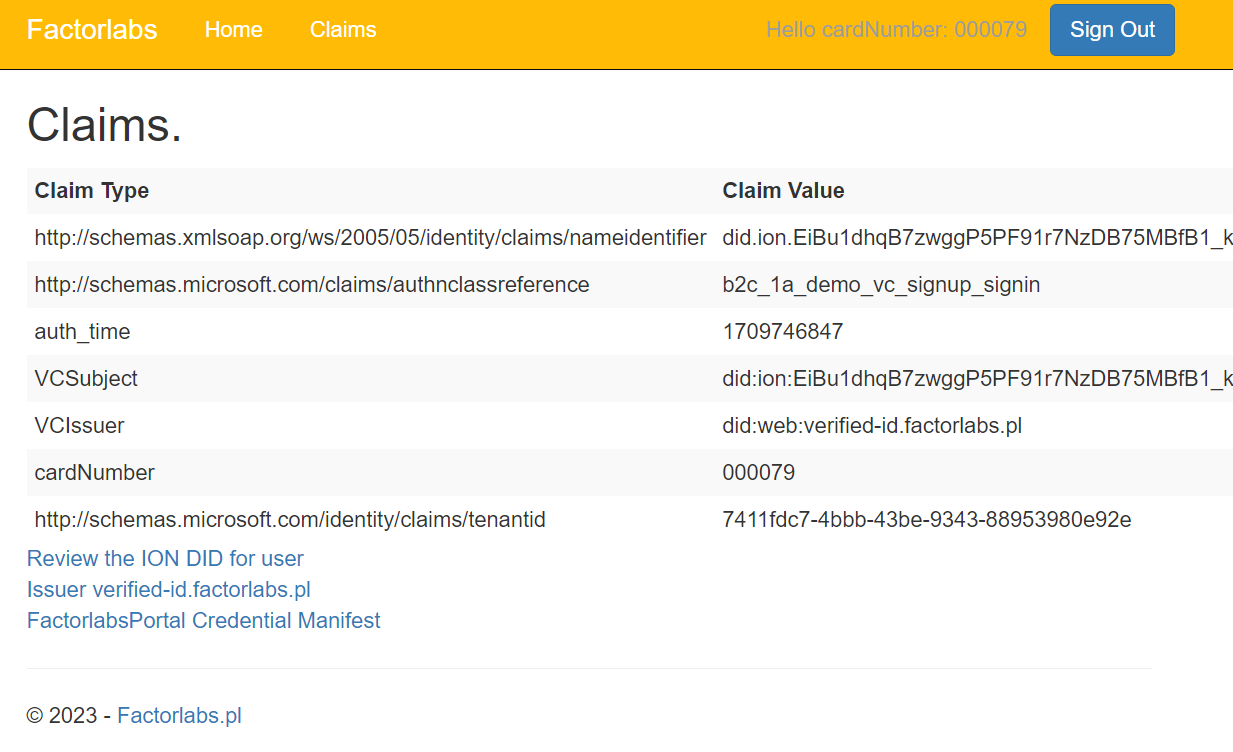
Review the ION DID for the user- you can check the DID Document for the user. -FactorlabsPortal Credential Manifest- the link to the manifest for the Credential - please use jwt.io to decode the token.
Motto for the integration

Products with Ingredients
Specification:
- Self-service to generate ingredient certificates as Verifiable Credentials
- Based on the list of ingredients, you can build the product certificate - next VC
- It is a simple chain of data, but you can use it to build an owner identity for the product - imagine that with the device (ingredient in my case), you can sign in to the device ecosystem, a similar case to the premium card on the airport to enter the lounge. Technology is on our side.
Visa and MasterCard will be useless
Account-to-account (A2A) money wire via Verifiable Credentials Presentation Flow is the next possible business case for the framework! One potential business case for VC is in Account to Account (A2A) money wire transfers. A2A transfers rely on a complex web of intermediaries to ensure the money is sent to the correct destination. Transfer can be time-consuming and expensive (fee from 3rd party service), and fraud or error is always risky. However, we can streamline the A2A transfer process using VC and reduce the intermediaries involved. The sender would present their Verifiable Credential to the recipient, who could verify the credential’s authenticity and complete the transfer. The process would be faster, more efficient, and more secure. Check the draft document for the flow.
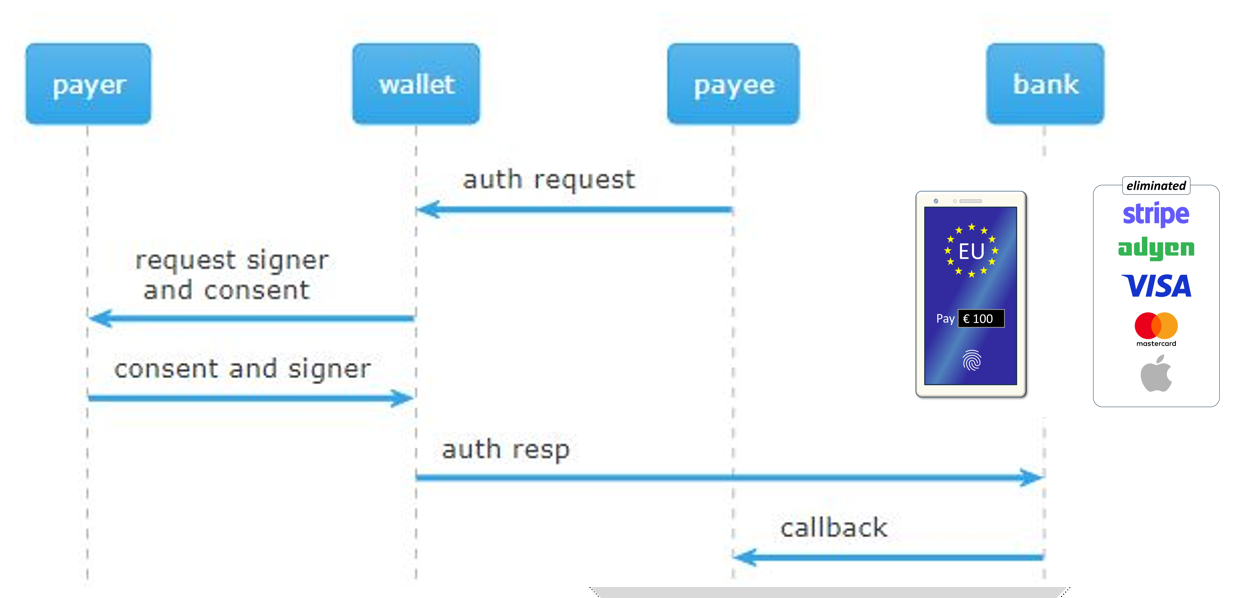
Is it a new standard/framework?
Presentation request
It is based on the OpenID Connect. How do I check it?
Open the browser with the link https://vc.factorlabs.pl/present/verifiedEmployee.html; in the network tab, you can find POST request; the response QR code contains the ‘presentation’ request for the wallet like below:
openid-vc://?request_uri=https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/presentationRequests/af87541f-f60c-43da-a0d3-4541c99023a8
Microsoft Entra Verified ID supports the following open standards: document link
A sample presentation request (JWT) so decoded from base64:
{
"jti": "9a06e250-3344-419b-a0ad-a5c7f16ce82c",
"iat": 1709672239,
"response_type": "id_token",
"response_mode": "post",
"scope": "openid",
"nonce": "HflTNHCZFLZ4pObpDqClKw==",
"redirect_uri": "https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/verifyPresentation",
"registration": {
"client_name": "Factorlabs",
"subject_syntax_types_supported": [
"did:ion"
],
"vp_formats": {
"jwt_vp": {
"alg": [
"ES256",
"ES256K",
"EdDSA"
]
},
"jwt_vc": {
"alg": [
"ES256",
"ES256K",
"EdDSA"
]
}
}
},
"client_id": "did:web:verified-id.factorlabs.pl",
"state": "djMBRg5e2d8iHSCPiOLMOzLr/nEMK+tc1M5r/3AhDwNrcQDhLMQiytftQVipSIakl2ZZP8Vq803X+qUVoeITtMspD5XEUZwBNS3X/6x4MG9wgFYunDYsDL18gOPA0KUELPD59tmoXEVaQ10gV3aXrCXfChWflLtEKEu0gT4saR+IxjB5Q+yld6IUrRuY+KhF9Qmp1oVNuQAGcm964OKXcs7Jt1Tf4CcreS29S6atXUraYtXEj+FgCbZl69LJiGCGqIOWgvZIQjkqXn6/1NxRYAlfTP5JtA2Y+J44nw2To03zuh2mTlLy5rmdugdAn6W7c890bg9dLQcf+LVbV7XEjk4gWNyrZdKi28Rvi6uwnPJS52z5SXCQOq/M0y4S2C59V49NL++l55n6JiNxWCO9ReYM1Nm/osat4JQIjsmyBsAlfuTIORo5jw0ZH4YOFj9CHUGoM/q5K3ktu7h0u0oNKnRisa3zh+2f7iwg19ck18+QmwmTcgBIuLQo9m6cbXMesus/liS5s765uQhdfA65uXS7gx0aahMgkh8PAy5h4gfPXvXreU68nhM7UuAJu6RdRYVP9kgWltSNVL0e64s+gULnnFJg0ytu0WcPWN5mzxmZo9Oocb1pKeMLSv0cxyBEQeWktZ+r4Vxmx5k0bTiwofN+aC/nYqMkh4N58LBRGj/y7yibCrzlPYHMrqjFqzUGilD85FfFlVJzbkSJloCNpum0lQ7CsuhH7xviYGPYuJcdosxlO+iWqb1t/82hK2+20iroc6XMjfB2boM07WwBT2W9Vb2IBqxxaOPYiQr25aWQBFo4zkYeqrj+N6yFGKrciOrAVHvR5q27ZPOcCRuDEgWQN30B8bUJNjrZdO0KvIpIgwTaHmgmw1hkV8R1SSurXxKCzU7XZXjsR/4LlB3bJHD1Er85gN3BLwvieMX7ATfk1mRBLDMvBfwj2yb4NLPcuU7bRjPq3TVVpY3pSVvwJVSe2eb8YyvO8+KsloM5BXG55L0n1DPIzQ==",
"exp": 1709672539,
"claims": {
"vp_token": {
"presentation_definition": {
"id": "7bbc5ed7-eb83-483d-a953-9c36b0188731",
"input_descriptors": [
{
"id": "45eae9e0-f0cf-4657-a491-9eaa7e131d3a",
"name": "VerifiedEmployee",
"purpose": "Hey Factorlabs user! Please share with us your Digital Identity",
"schema": [
{
"uri": "VerifiedEmployee"
}
]
}
]
}
}
}
}
So, as you can see, there is a connection with the OpenID Connect.
Issuance process
We also have the QR code, but behind the scenes, the JWT token contains:
{
"jti": "4398408a-728f-4dc3-8dc1-14e6502ebcf6",
"iat": 1715114172,
"response_type": "id_token",
"response_mode": "post",
"scope": "openid",
"nonce": "qLlL0WXWvb16lddY3B8U/A==",
"client_id": "did:web:verified-id.factorlabs.pl",
"redirect_uri": "https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/completeIssuance",
"prompt": "create",
"state": "djOimvObyJ3/8z7ggInS85vdT6wnf+vSOUmcEHVIB8OCunYzy/H1e7cFY3LXlWFXym39vtJBMTbZWv75LHFnx9cP3YrtpJ/WSKVwzsHUsQVsJdmF26cCMgjEocelQaWlvT6NHC5TG5HTFF9HyNnlq88QCCdk6yHEan8xGmHUD3N2/ioiaAxw+EYSKVPLth0v9HlKOoiDzzu/Snt5vyAvBu5lvdEWPSvK/kSs7BFVQsWNEhB8HlENKsbuVLOKx4T+uSVCaB5AQdSYXU9lAJwriKvP8XZ7WKGmYvq9QuCA26D7egQpTM2UMcStBsuJxmBEdsns15APlBjIOa7PWP357RVxQLDdAolhLTk4vtC6r52rv98r/d2+aPwOfqPmk+3ks+TcjX1kJzhW+28GTjb+Eru4roT8N1kNZyZl80/yS9KzhhEiUwVlVUKBLVDCd5qEU0iK49abIVbL6G62gSpx3flO/lsJUsVHqA==",
"exp": 1715114472,
"registration": {
"client_name": "Factorlabs",
"subject_syntax_types_supported": [
"did:ion"
],
"vp_formats": {
"jwt_vp": {
"alg": [
"ES256K"
]
},
"jwt_vc": {
"alg": [
"ES256K"
]
}
}
},
"claims": {
"vp_token": {
"presentation_definition": {
"id": "5bdeea3f-98ca-4781-9ba4-6d9504f422d7",
"input_descriptors": [
{
"id": "FactorlabsIngredientCarbonprint",
"schema": [
{
"uri": "FactorlabsIngredientCarbonprint"
}
],
"issuance": [
{
"manifest": "https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/contracts/8333b282-b6a1-df0e-5a19-492ef9e339b3/manifest"
}
]
}
]
}
}
},
"pin": {
"length": 4,
"type": "numeric",
"alg": "sha256",
"iterations": 1,
"salt": "1cde51e9c95541cfba489a1a4bee59a6",
"hash": "dm+N+wLLJlGhvkbqLygeU4F65J/kC/Zp4/vcuv846o4="
},
"id_token_hint": "eyJhbGciOiJFUzI1NksiLCJraWQiOiJkaWQ6d2ViOnZlcmlmaWVkLWlkLmZhY3RvcmxhYnMucGwjNWQzYjYxMjdiNjJlNGU4ODhjMmZjNmJlOTVlNzk4MjV2Y1NpZ25pbmdLZXktMmIwYjkiLCJ0eXAiOiJKV1QifQ.eyJzdWIiOiJ0dkVzSkEzTEJDaGg0LXNKTGJCaHBhTTJ0TEVLWU9sSlczOGIySS15RUhRIiwiYXVkIjoiaHR0cHM6Ly9iZXRhLmV1LmRpZC5tc2lkZW50aXR5LmNvbS92MS4wL3RlbmFudHMvNjc5MGZhZGYtOTc1MS00ZjczLThmNjUtODQ0Njc1YjlhMjJhL3ZlcmlmaWFibGVDcmVkZW50aWFscy9pc3N1ZSIsIm5vbmNlIjoid3h1UFl1NzI3QlJUYUtUNzdKWlQzUT09Iiwic3ViX2p3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJkaWQ6d2ViOnZlcmlmaWVkLWlkLmZhY3RvcmxhYnMucGwjNWQzYjYxMjdiNjJlNGU4ODhjMmZjNmJlOTVlNzk4MjV2Y1NpZ25pbmdLZXktMmIwYjkiLCJrdHkiOiJFQyIsIngiOiJUV3dwNUE0M3oydmptbmRHOS1BR3NxWVU4bENMWkFwUWJPRmJFejRfcklFIiwieSI6Ik1wT0twb09VZnJJZExYeEFCbE9EMDNESTBTd3Zyc25xVXBOYjVQN1B4YWsifSwiZGlkIjoiZGlkOndlYjp2ZXJpZmllZC1pZC5mYWN0b3JsYWJzLnBsIiwiY2FyYm9ucHJpbnRuYW1lIjoiQURGWDo0OTozODU6MzE0OjI0IiwiY2FyYm9ucHJpbnR2YWx1ZSI6IjIwOCIsImlzcyI6Imh0dHBzOi8vc2VsZi1pc3N1ZWQubWUiLCJpYXQiOjE3MTUxMTQxNzIsImp0aSI6IjQzOTg0MDhhLTcyOGYtNGRjMy04ZGMxLTE0ZTY1MDJlYmNmNiIsImV4cCI6MTcxNTExNDQ3MiwicGluIjp7Imxlbmd0aCI6NCwidHlwZSI6Im51bWVyaWMiLCJhbGciOiJzaGEyNTYiLCJpdGVyYXRpb25zIjoxLCJzYWx0IjoiMWNkZTUxZTljOTU1NDFjZmJhNDg5YTFhNGJlZTU5YTYiLCJoYXNoIjoiZG0rTit3TExKbEdodmticUx5Z2VVNEY2NUova0MvWnA0L3ZjdXY4NDZvND0ifX0.Am0jUMyI-BzvxWjpnNPNebp_VQ44iuaod5DoNOLR8igG4uR0Brq4AtoAUUWgr-AB4qOhrM2fpc8ljT70__2h5A"
}
Inside id token hint is:
{
"sub": "tvEsJA3LBChh4-sJLbBhpaM2tLEKYOlJW38b2I-yEHQ",
"aud": "https://beta.eu.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/issue",
"nonce": "wxuPYu727BRTaKT77JZT3Q==",
"sub_jwk": {
"crv": "secp256k1",
"kid": "did:web:verified-id.factorlabs.pl#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9",
"kty": "EC",
"x": "TWwp5A43z2vjmndG9-AGsqYU8lCLZApQbOFbEz4_rIE",
"y": "MpOKpoOUfrIdLXxABlOD03DI0SwvrsnqUpNb5P7Pxak"
},
"did": "did:web:verified-id.factorlabs.pl",
"carbonprintname": "ADFX:49:385:314:24",
"carbonprintvalue": "208",
"iss": "https://self-issued.me",
"iat": 1715114172,
"jti": "4398408a-728f-4dc3-8dc1-14e6502ebcf6",
"exp": 1715114472,
"pin": {
"length": 4,
"type": "numeric",
"alg": "sha256",
"iterations": 1,
"salt": "1cde51e9c95541cfba489a1a4bee59a6",
"hash": "dm+N+wLLJlGhvkbqLygeU4F65J/kC/Zp4/vcuv846o4="
}
}
Do you want to try it?
Build your test environment
Check GitHub repository with the sample implementation. The easiest way to start is to use the Microsoft Authenticator as a wallet. By default, you can:
- store and present VC’s
- check the activities per credential, each presentation with audit log, like in the pictures below
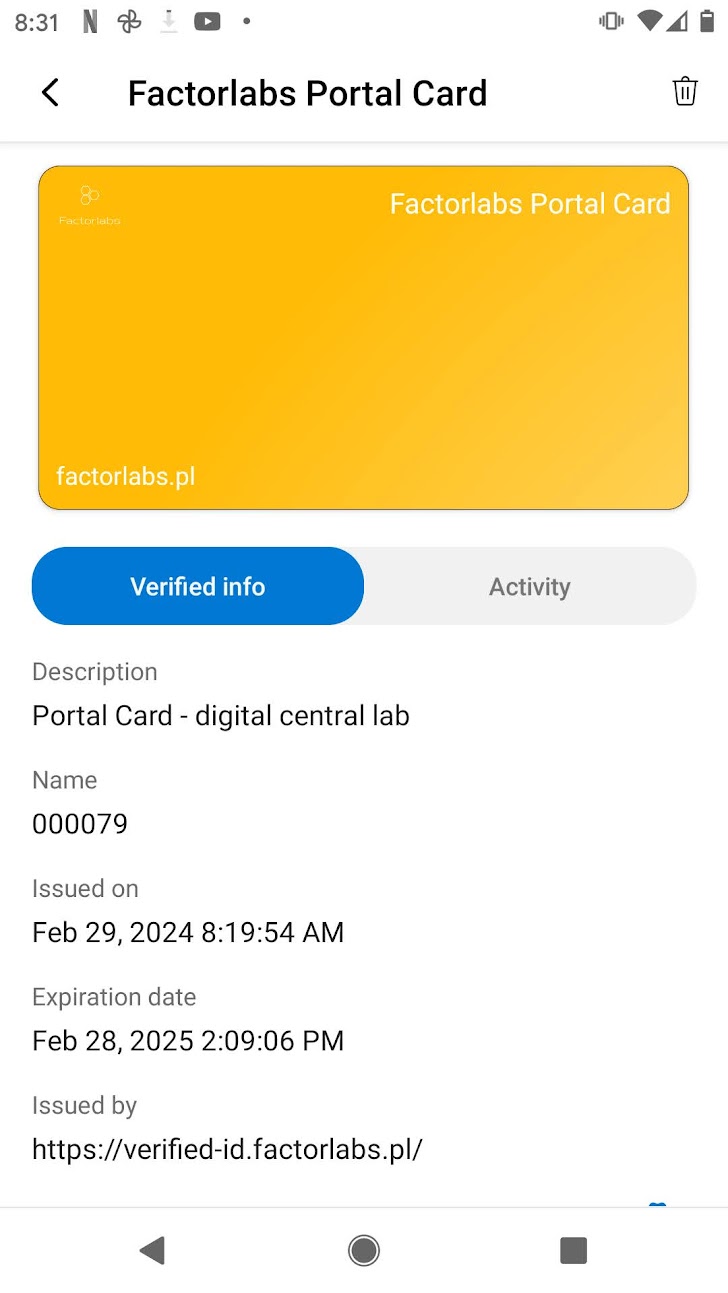
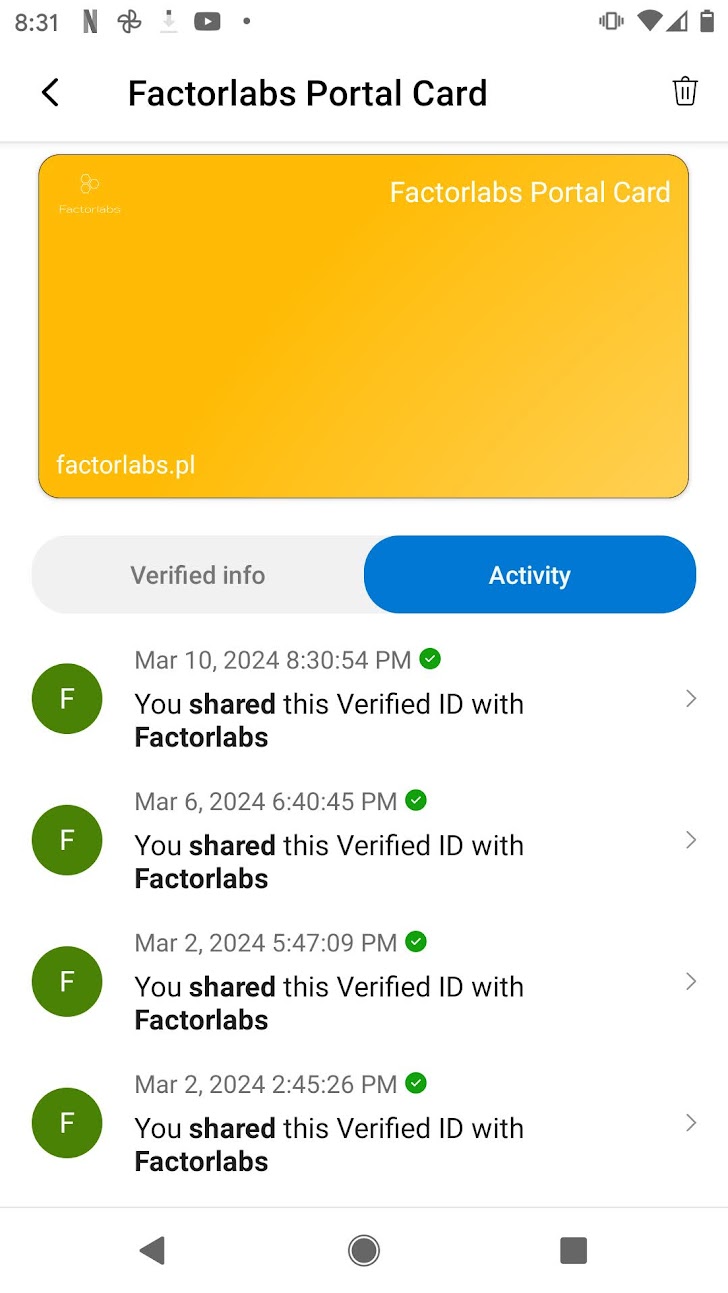
- use Face Check during the presentation - the process uses the picture stored in the VC Claim - and via Azure Cognitive Services checks the picture and scans the face. As a note, the image is not from the Entra ID account but stored from the VC Claim in the digital wallet on the mobile phone.
Links
- All my VC pages are for you in one place
- Entra Verified ID documentation link
- Entra Verified ID technical start point
- Account To Account flow
- Microsoft Sample Implementation Github repository
MS Documentation
- News/new features https://learn.microsoft.com/en-us/entra/verified-id/whats-new
- Supported standards https://learn.microsoft.com/en-us/entra/verified-id/verifiable-credentials-standards
