History
- 2024-06-17: Added Wallet SDK Link & Sample Android Implementation.
- 2024-06-30: Small changes.
- 2025-07-23: fixed verified employee demo link and removed face check demo.
- 2025-07-27: Improved B2C and wallet example, improved structure.
Entra Verified ID: Complete Guide with Hands-On Workshop
Introduction
In our digital world, identity verification remains fragmented across countless systems, creating security risks, privacy concerns, and user friction. Microsoft Entra Verified ID solves these challenges using W3C-standard Verifiable Credentials, enabling secure, decentralized, and user-controlled digital identity.
This comprehensive guide takes you from concept to implementation through practical examples, working demos, and a complete hands-on workshop. You’ll learn how Verifiable Credentials work, see real-world applications, and build your own solutions.
Get Started Immediately
Want to dive right in? Use my GitHub repository to set up your first Verifiable Credential system:
The workshop provides step-by-step instructions with code examples and detailed explanations for creating a complete Verifiable Credentials flow.
Understanding Verifiable Credentials: From Physical to Digital
The Physical World Analogy
Consider your national ID card - a perfect example of how identity verification works:
The Process:
- You visit a government office with supporting documents
- Officials verify your identity using existing credentials
- The government issues an official ID card
- You carry this card in your wallet
- Anyone can verify your identity by checking the card’s authenticity
Key Components:
- Issuer: Government (trusted authority)
- Holder: You (with the card in your wallet)
- Verifier: Anyone who needs to confirm your identity
- Trust: Government authority and anti-counterfeiting features
The Digital Transformation
Verifiable Credentials bring this same trust model to the digital world, but with enhanced capabilities:
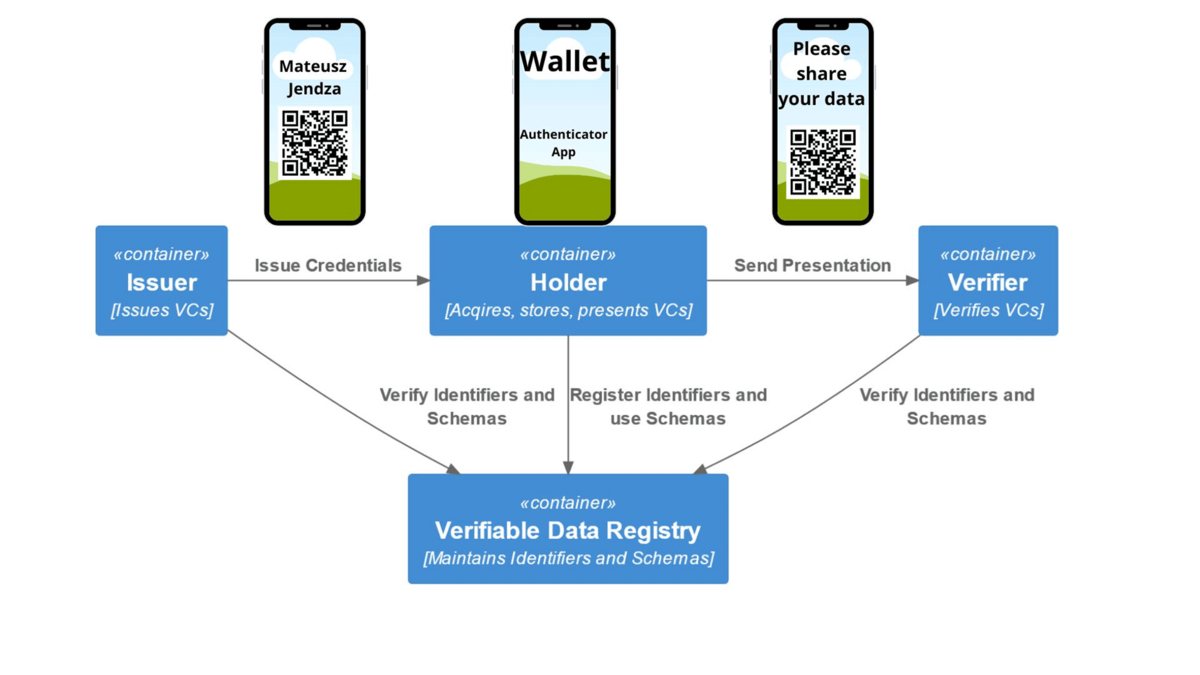
Digital Entities:
- Issuer: Government, bank, company, or organization using Entra ID
- Holder: You, with credentials stored in a digital wallet (like Microsoft Authenticator)
- Verifier: Any system that needs to verify your claims
- Trust: Cryptographic signatures and decentralized verification
Key Advantages:
- No central authority required for verification
- Enhanced privacy through selective disclosure
- Tamper-proof through cryptographic protection
- Instant verification anywhere in the world
How Security Works: Trust Without Central Control
Cryptographic Foundation
Verifiable Credentials use Public Key Infrastructure (PKI) to ensure security:
- Digital Signatures: Cryptographically prove credential authenticity
- Public Key Verification: Anyone can verify signatures using publicly available keys
- Tamper Detection: Any modification to a credential invalidates its signature
- Decentralized Trust: No need to contact the issuer for verification
The Verifiable Data Registry
Public key information is stored in decentralized registries:
- Issuers: Publish DID Documents to the web
- Holders: Store DID Documents on blockchain (ION network)
- Verifiers: Access public keys to verify credentials independently
Example: Issuer DID Document
You can verify issuer authenticity by checking their DID Document at: manifest
{
"id": "did:web:verified-id.factorlabs.pl",
"@context": [
"https://www.w3.org/ns/did/v1",
{
"@base": "did:web:verified-id.factorlabs.pl"
}
],
"service": [
{
"id": "#linkeddomains",
"type": "LinkedDomains",
"serviceEndpoint": {
"origins": [
"https://verified-id.factorlabs.pl/"
]
}
},
{
"id": "#hub",
"type": "IdentityHub",
"serviceEndpoint": {
"instances": [
"https://hub.did.msidentity.com/v1.0/6790fadf-9751-4f73-8f65-844675b9a22a"
]
}
}
],
"verificationMethod": [
{
"id": "#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9",
"controller": "did:web:verified-id.factorlabs.pl",
"type": "EcdsaSecp256k1VerificationKey2019",
"publicKeyJwk": {
"crv": "secp256k1",
"kty": "EC",
"x": "TWwp5A43z2vjmndG9-AGsqYU8lCLZApQbOFbEz4_rIE",
"y": "MpOKpoOUfrIdLXxABlOD03DI0SwvrsnqUpNb5P7Pxak"
}
}
],
"authentication": [
"#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9"
],
"assertionMethod": [
"#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9"
]
}
Holder Identity on Blockchain
Holders publish their DID Documents to the ION blockchain for decentralized verification. Here’s an example of my DID: ION Explorer Link
{
"@context": "https://w3id.org/did-resolution/v1",
"didDocument": {
"id": "did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsImt0eSI6IkVDIiwidXNlIjoic2lnIiwieCI6IlNRS2V0aFdnQWtocGNnaUR3czBaTXJDa2k5TzFIRVMtVmVhUTdmeFhSSU0iLCJ5IjoiUEZSTDZnNDROU0pXanlLQnlkRVZ2T1JDMm9qODV3bVFhR1B3bW1GREpYcyJ9LCJwdXJwb3NlcyI6WyJhdXRoZW50aWNhdGlvbiJdLCJ0eXBlIjoiRWNkc2FTZWNwMjU2azFWZXJpZmljYXRpb25LZXkyMDE5In1dfX1dLCJ1cGRhdGVDb21taXRtZW50IjoiRWlEYlR2ZG5sajBqdEJJcm9iNEJ2MVVMRnJJU0xnSkxyM3c2MHBENElYcWFxdyJ9LCJzdWZmaXhEYXRhIjp7ImRlbHRhSGFzaCI6IkVpRGRLSXdWdzNfZ2QtaWplNTVuLXdWQ3psczNwZUxITXVUczBPcU50blp2MFEiLCJyZWNvdmVyeUNvbW1pdG1lbnQiOiJFaUM1Y0FsaHlLRWNDejhzYWJidDVwLWpWSzNRSmt2cVdFVFQ5c0J5U2ctcW9nIn19",
"@context": [
"https://www.w3.org/ns/did/v1",
{
"@base": "did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsImt0eSI6IkVDIiwidXNlIjoic2lnIiwieCI6IlNRS2V0aFdnQWtocGNnaUR3czBaTXJDa2k5TzFIRVMtVmVhUTdmeFhSSU0iLCJ5IjoiUEZSTDZnNDROU0pXanlLQnlkRVZ2T1JDMm9qODV3bVFhR1B3bW1GREpYcyJ9LCJwdXJwb3NlcyI6WyJhdXRoZW50aWNhdGlvbiJdLCJ0eXBlIjoiRWNkc2FTZWNwMjU2azFWZXJpZmljYXRpb25LZXkyMDE5In1dfX1dLCJ1cGRhdGVDb21taXRtZW50IjoiRWlEYlR2ZG5sajBqdEJJcm9iNEJ2MVVMRnJJU0xnSkxyM3c2MHBENElYcWFxdyJ9LCJzdWZmaXhEYXRhIjp7ImRlbHRhSGFzaCI6IkVpRGRLSXdWdzNfZ2QtaWplNTVuLXdWQ3psczNwZUxITXVUczBPcU50blp2MFEiLCJyZWNvdmVyeUNvbW1pdG1lbnQiOiJFaUM1Y0FsaHlLRWNDejhzYWJidDVwLWpWSzNRSmt2cVdFVFQ5c0J5U2ctcW9nIn19"
}
],
"verificationMethod": [
{
"id": "#ba6bddbe642d439c96b15ea72ed5a887",
"controller": "did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJiYTZiZGRiZTY0MmQ0MzljOTZiMTVlYTcyZWQ1YTg4NyIsImt0eSI6IkVDIiwidXNlIjoic2lnIiwieCI6IlNRS2V0aFdnQWtocGNnaUR3czBaTXJDa2k5TzFIRVMtVmVhUTdmeFhSSU0iLCJ5IjoiUEZSTDZnNDROU0pXanlLQnlkRVZ2T1JDMm9qODV3bVFhR1B3bW1GREpYcyJ9LCJwdXJwb3NlcyI6WyJhdXRoZW50aWNhdGlvbiJdLCJ0eXBlIjoiRWNkc2FTZWNwMjU2azFWZXJpZmljYXRpb25LZXkyMDE5In1dfX1dLCJ1cGRhdGVDb21taXRtZW50IjoiRWlEYlR2ZG5sajBqdEJJcm9iNEJ2MVVMRnJJU0xnSkxyM3c2MHBENElYcWFxdyJ9LCJzdWZmaXhEYXRhIjp7ImRlbHRhSGFzaCI6IkVpRGRLSXdWdzNfZ2QtaWplNTVuLXdWQ3psczNwZUxITXVUczBPcU50blp2MFEiLCJyZWNvdmVyeUNvbW1pdG1lbnQiOiJFaUM1Y0FsaHlLRWNDejhzYWJidDVwLWpWSzNRSmt2cVdFVFQ5c0J5U2ctcW9nIn19",
"type": "EcdsaSecp256k1VerificationKey2019",
"publicKeyJwk": {
"crv": "secp256k1",
"kid": "ba6bddbe642d439c96b15ea72ed5a887",
"kty": "EC",
"use": "sig",
"x": "SQKethWgAkhpcgiDws0ZMrCki9O1HES-VeaQ7fxXRIM",
"y": "PFRL6g44NSJWjyKBydEVvORC2oj85wmQaGPwmmFDJXs"
}
}
],
"authentication": [
"#ba6bddbe642d439c96b15ea72ed5a887"
]
},
"didDocumentMetadata": {
"method": {
"published": false,
"recoveryCommitment": "EiC5cAlhyKEcCz8sabbt5p-jVK3QJkvqWETT9sBySg-qog",
"updateCommitment": "EiDbTvdnlj0jtBIrob4Bv1ULFrISLgJLr3w60pD4IXqaqw"
},
"equivalentId": [
"did:ion:EiBu1dhqB7zwggP5PF91r7NzDB75MBfB1_k4lXlPHVWs2w"
]
}
}
Real-World Applications and Live Demos
I’ve created multiple working demonstrations that you can test immediately. Visit the demo portal to explore different Verifiable Credential scenarios.
1. Verified Employee Credentials
Business Challenge: Organizations need secure, verifiable employee identification that works across systems and partners without exposing sensitive HR data.
Solution: Employee credentials issued through Entra ID that can be verified anywhere without contacting the issuer.
Key Benefits:
- Reduced identity verification costs
- Enhanced security through cryptographic proof
- Privacy-preserving identity sharing
- Seamless integration with existing systems
- Built-in Face Check capabilities for enhanced security
How It Works:
You can issue employee credentials in two ways:
- Microsoft My Account Integration: Users can issue credentials directly from My Account after enabling Entra Verified ID
- Custom Application: Organizations can build custom issuance flows using ID token hints
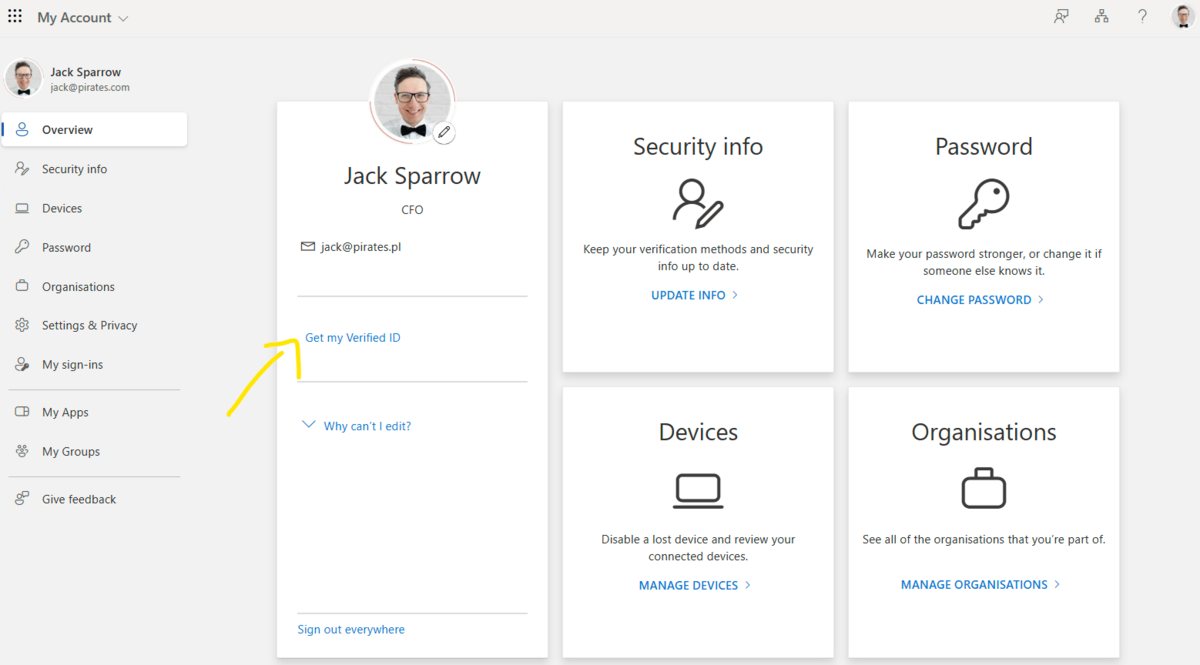
Try It Yourself:
- **Issue Employee Credential **: via My Account
- Verify Employee Credential: Presentation with DEMO page
Special Feature: The Verified Employee credential includes Face Check capability, using the photo stored in the credential (not your account) combined with Azure Cognitive Services for real-time verification.
Sidenote
We can issue credential based on the ID Token Hint (ID Token for example) - on the screen below on the right side we can see the flow with the Signing In activity:
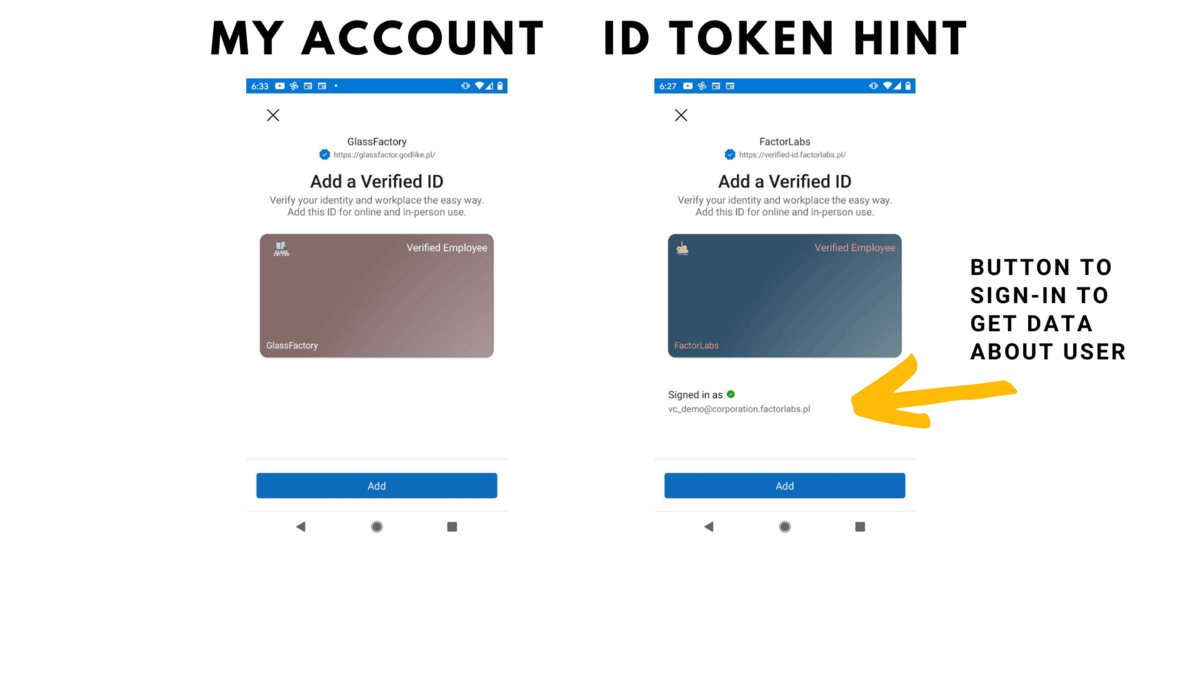
2. Passwordless Authentication with Azure AD B2C
Business Challenge: Traditional password-based authentication creates security vulnerabilities, user friction, and support overhead.
Solution: Complete passwordless sign-up and sign-in flows using Verifiable Credentials as authentication keys.

Implementation Features:
- Complete Azure AD B2C integration
- Invitation-based account creation
- No stored user data (email, phone, passwords)
- MS Authenticator App integration
- Factorlabs Dedicated Wallet integration
- One seamless flow: sign-in → credential issuance → passwordless authentication
Business Scenario: Invitation-only systems where access is granted through Verifiable Credentials, perfect for exclusive services, partner portals, or premium applications.
Live Demo: Portal Factorlabs:
Start page with the Sign In button
User details page with ION Subject Identifier for user
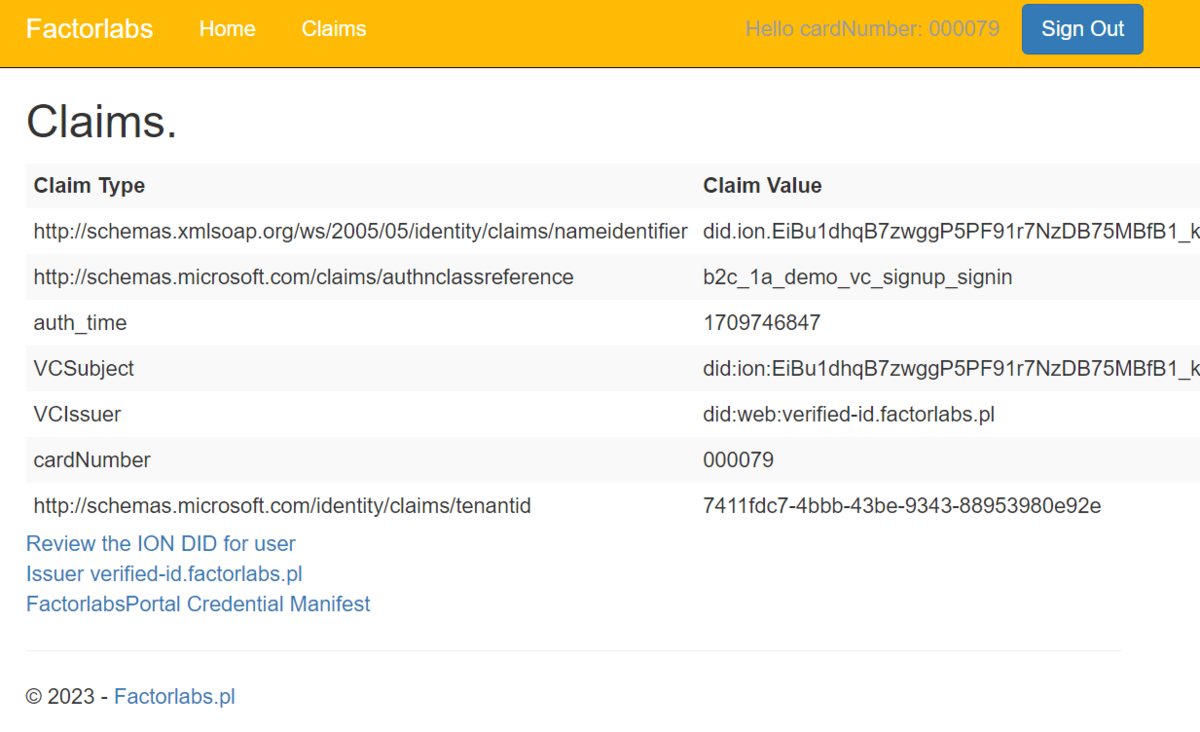
Demo Features:
- Review the ION DID for authenticated users
- Inspect the credential manifest structure
- Experience complete passwordless flow

Factorlabs VC Wallet
With dedicated Factorlabs VC Wallet, you can manage your Verifiable Credentials, including Azure AD B2C credentials and Bank Account.
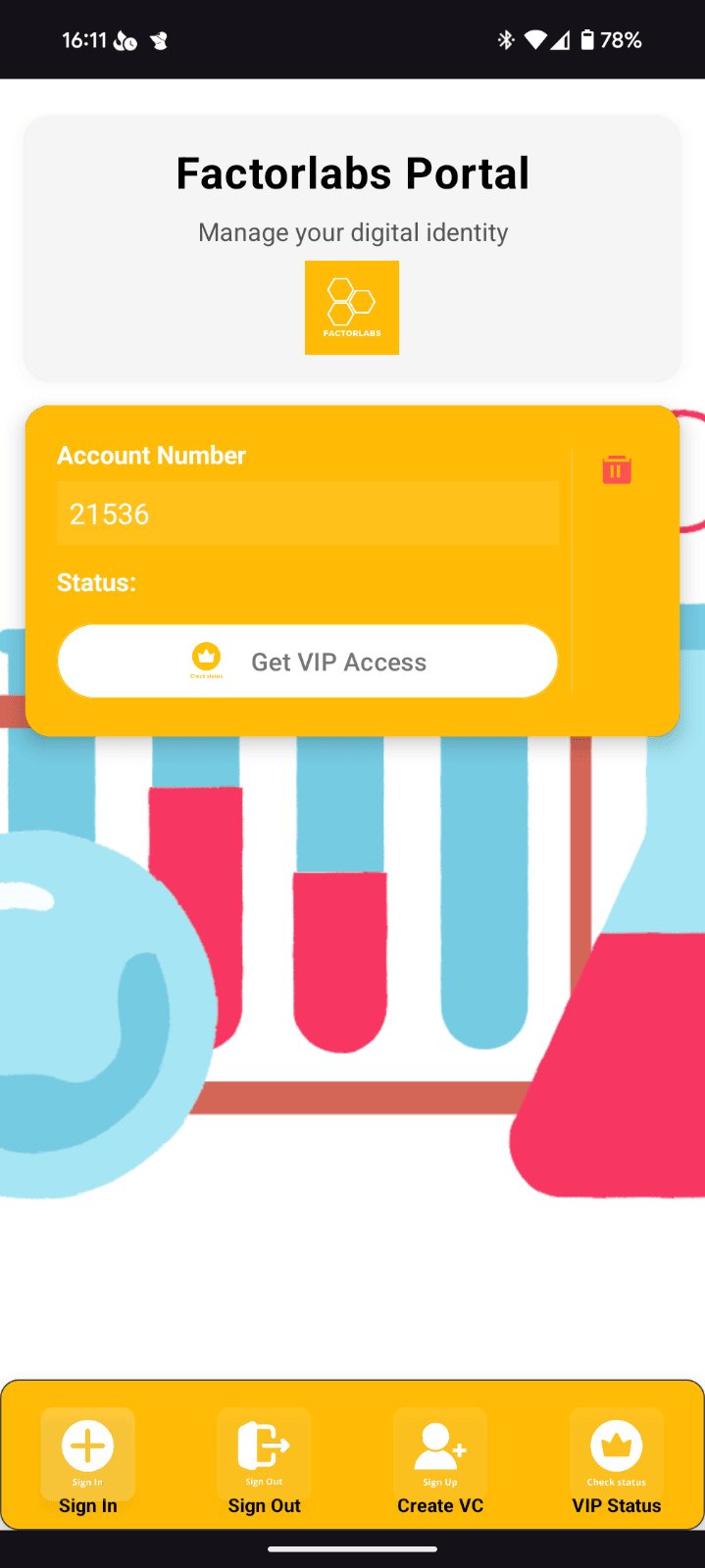
Demo Features:
- Azure AD B2C is only technical component to protect API and WebSite.
- id_token_hint provides passwordless authentication - without Azure AD B2C screen.
- Dedicated button on the website with the Wallet integration.
- Wallet SDK used to operate with Entra Verified ID.
3. Supply Chain Verification: Products and Ingredients
Business Challenge: Supply chain transparency and product authenticity verification require complex, expensive systems that don’t scale.
Solution: Self-service ingredient certification system where individual components can be verified and combined into product certificates.
How It Works:
- Generate ingredient certificates as Verifiable Credentials
- Combine ingredients to build product certificates
- Create verifiable ownership chains for complex products
- Enable device-level authentication (similar to premium airport lounge access)
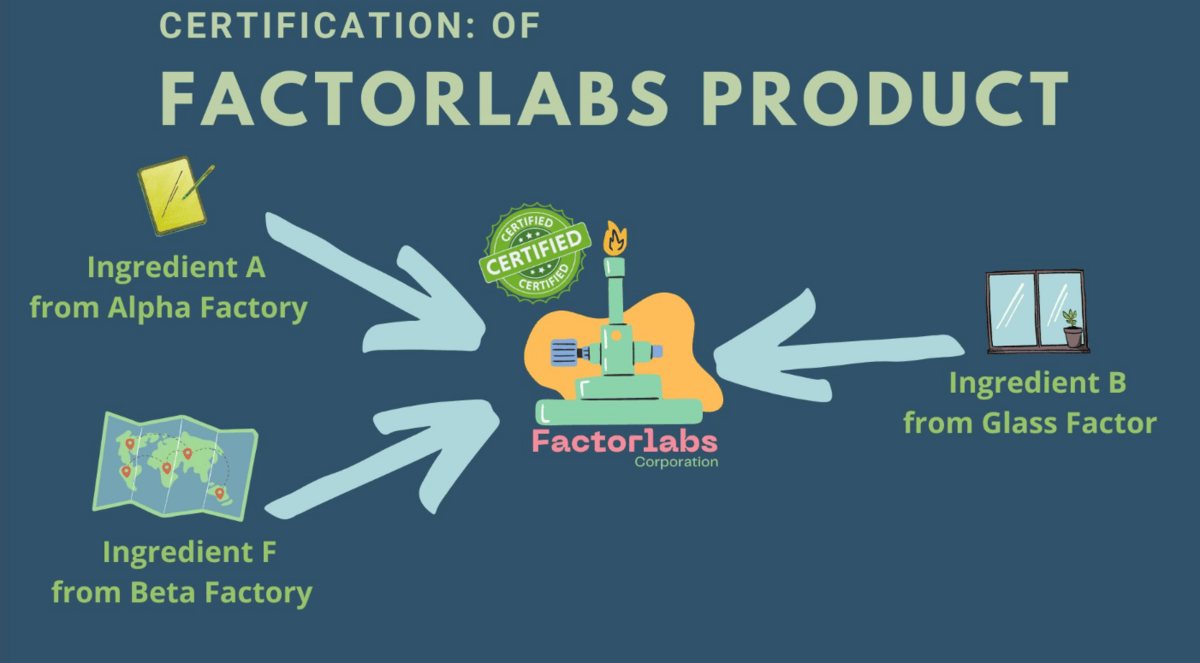
Try the Demo: sorry - today disabled :(
Business Applications:
- Food safety and origin verification
- Pharmaceutical supply chain tracking
- Luxury goods authenticity
- IoT device ecosystem access control
- Keyless entry systems (for homes and cars)
4. Future Application: Account-to-Account Payments
Vision: Replace traditional payment card networks with direct, cryptographically verified account-to-account transfers.
Current Problem: A2A transfers rely on complex intermediary networks, creating delays, fees, and fraud risks.
Verifiable Credential Solution:
- Senders present cryptographically verified credentials
- Recipients verify authenticity instantly
- Transfers complete faster with lower costs
- Reduced fraud through cryptographic proof
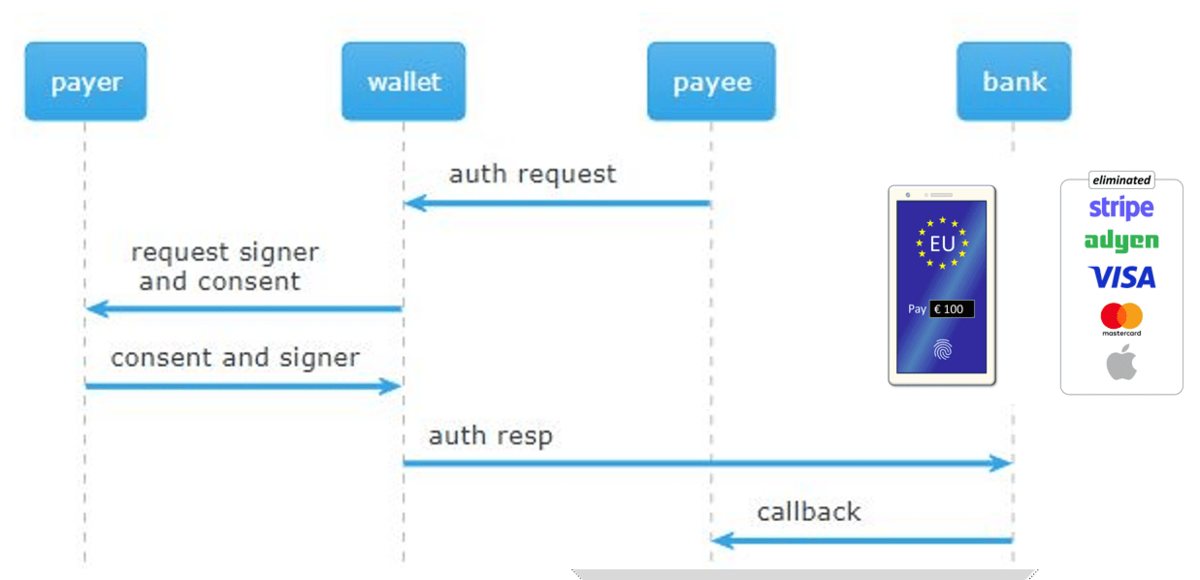
Technical Foundation: Check the draft specification for payment presentation flows.
Technical Deep Dive: Standards and Implementation
Built on Open Standards
Microsoft Entra Verified ID implements multiple W3C and industry standards:
W3C Standards:
- Verifiable Credentials Data Model (November 2019)
- Decentralized Identifiers (DIDs)
- JSON-LD for structured data
OpenID Connect Integration: All credential flows use OpenID Connect protocols. Here’s how to verify this yourself:
- Open the presentation demo
- Check the browser network tab for the POST request
- Examine the QR code content
Example Presentation Request:
openid-vc://?request_uri=https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/presentationRequests/af87541f-f60c-43da-a0d3-4541c99023a8
Decoded Presentation Request JWT:
{
"jti": "9a06e250-3344-419b-a0ad-a5c7f16ce82c",
"iat": 1709672239,
"response_type": "id_token",
"response_mode": "post",
"scope": "openid",
"nonce": "HflTNHCZFLZ4pObpDqClKw==",
"redirect_uri": "https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/verifyPresentation",
"registration": {
"client_name": "Factorlabs",
"subject_syntax_types_supported": [
"did:ion"
],
"vp_formats": {
"jwt_vp": {
"alg": [
"ES256",
"ES256K",
"EdDSA"
]
},
"jwt_vc": {
"alg": [
"ES256",
"ES256K",
"EdDSA"
]
}
}
},
"client_id": "did:web:verified-id.factorlabs.pl",
"state": "djMBRg5e2d8iHSCPiOLMOzLr/nEMK+tc1M5r/3AhDwNrcQDhLMQiytftQVipSIakl2ZZP8Vq803X+qUVoeITtMspD5XEUZwBNS3X/6x4MG9wgFYunDYsDL18gOPA0KUELPD59tmoXEVaQ10gV3aXrCXfChWflLtEKEu0gT4saR+IxjB5Q+yld6IUrRuY+KhF9Qmp1oVNuQAGcm964OKXcs7Jt1Tf4CcreS29S6atXUraYtXEj+FgCbZl69LJiGCGqIOWgvZIQjkqXn6/1NxRYAlfTP5JtA2Y+J44nw2To03zuh2mTlLy5rmdugdAn6W7c890bg9dLQcf+LVbV7XEjk4gWNyrZdKi28Rvi6uwnPJS52z5SXCQOq/M0y4S2C59V49NL++l55n6JiNxWCO9ReYM1Nm/osat4JQIjsmyBsAlfuTIORo5jw0ZH4YOFj9CHUGoM/q5K3ktu7h0u0oNKnRisa3zh+2f7iwg19ck18+QmwmTcgBIuLQo9m6cbXMesus/liS5s765uQhdfA65uXS7gx0aahMgkh8PAy5h4gfPXvXreU68nhM7UuAJu6RdRYVP9kgWltSNVL0e64s+gULnnFJg0ytu0WcPWN5mzxmZo9Oocb1pKeMLSv0cxyBEQeWktZ+r4Vxmx5k0bTiwofN+aC/nYqMkh4N58LBRGj/y7yibCrzlPYHMrqjFqzUGilD85FfFlVJzbkSJloCNpum0lQ7CsuhH7xviYGPYuJcdosxlO+iWqb1t/82hK2+20iroc6XMjfB2boM07WwBT2W9Vb2IBqxxaOPYiQr25aWQBFo4zkYeqrj+N6yFGKrciOrAVHvR5q27ZPOcCRuDEgWQN30B8bUJNjrZdO0KvIpIgwTaHmgmw1hkV8R1SSurXxKCzU7XZXjsR/4LlB3bJHD1Er85gN3BLwvieMX7ATfk1mRBLDMvBfwj2yb4NLPcuU7bRjPq3TVVpY3pSVvwJVSe2eb8YyvO8+KsloM5BXG55L0n1DPIzQ==",
"exp": 1709672539,
"claims": {
"vp_token": {
"presentation_definition": {
"id": "7bbc5ed7-eb83-483d-a953-9c36b0188731",
"input_descriptors": [
{
"id": "45eae9e0-f0cf-4657-a491-9eaa7e131d3a",
"name": "VerifiedEmployee",
"purpose": "Hey Factorlabs user! Please share with us your Digital Identity",
"schema": [
{
"uri": "VerifiedEmployee"
}
]
}
]
}
}
}
}
Credential Issuance Flow
Issuance Request Structure:
{
"jti": "4398408a-728f-4dc3-8dc1-14e6502ebcf6",
"iat": 1715114172,
"response_type": "id_token",
"response_mode": "post",
"scope": "openid",
"nonce": "qLlL0WXWvb16lddY3B8U/A==",
"client_id": "did:web:verified-id.factorlabs.pl",
"redirect_uri": "https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/completeIssuance",
"prompt": "create",
"state": "djOimvObyJ3/8z7ggInS85vdT6wnf+vSOUmcEHVIB8OCunYzy/H1e7cFY3LXlWFXym39vtJBMTbZWv75LHFnx9cP3YrtpJ/WSKVwzsHUsQVsJdmF26cCMgjEocelQaWlvT6NHC5TG5HTFF9HyNnlq88QCCdk6yHEan8xGmHUD3N2/ioiaAxw+EYSKVPLth0v9HlKOoiDzzu/Snt5vyAvBu5lvdEWPSvK/kSs7BFVQsWNEhB8HlENKsbuVLOKx4T+uSVCaB5AQdSYXU9lAJwriKvP8XZ7WKGmYvq9QuCA26D7egQpTM2UMcStBsuJxmBEdsns15APlBjIOa7PWP357RVxQLDdAolhLTk4vtC6r52rv98r/d2+aPwOfqPmk+3ks+TcjX1kJzhW+28GTjb+Eru4roT8N1kNZyZl80/yS9KzhhEiUwVlVUKBLVDCd5qEU0iK49abIVbL6G62gSpx3flO/lsJUsVHqA==",
"exp": 1715114472,
"registration": {
"client_name": "Factorlabs",
"subject_syntax_types_supported": [
"did:ion"
],
"vp_formats": {
"jwt_vp": {
"alg": [
"ES256K"
]
},
"jwt_vc": {
"alg": [
"ES256K"
]
}
}
},
"claims": {
"vp_token": {
"presentation_definition": {
"id": "5bdeea3f-98ca-4781-9ba4-6d9504f422d7",
"input_descriptors": [
{
"id": "FactorlabsIngredientCarbonprint",
"schema": [
{
"uri": "FactorlabsIngredientCarbonprint"
}
],
"issuance": [
{
"manifest": "https://verifiedid.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/contracts/8333b282-b6a1-df0e-5a19-492ef9e339b3/manifest"
}
]
}
]
}
}
},
"pin": {
"length": 4,
"type": "numeric",
"alg": "sha256",
"iterations": 1,
"salt": "1cde51e9c95541cfba489a1a4bee59a6",
"hash": "dm+N+wLLJlGhvkbqLygeU4F65J/kC/Zp4/vcuv846o4="
},
"id_token_hint": "eyJhbGciOiJFUzI1NksiLCJraWQiOiJkaWQ6d2ViOnZlcmlmaWVkLWlkLmZhY3RvcmxhYnMucGwjNWQzYjYxMjdiNjJlNGU4ODhjMmZjNmJlOTVlNzk4MjV2Y1NpZ25pbmdLZXktMmIwYjkiLCJ0eXAiOiJKV1QifQ.eyJzdWIiOiJ0dkVzSkEzTEJDaGg0LXNKTGJCaHBhTTJ0TEVLWU9sSlczOGIySS15RUhRIiwiYXVkIjoiaHR0cHM6Ly9iZXRhLmV1LmRpZC5tc2lkZW50aXR5LmNvbS92MS4wL3RlbmFudHMvNjc5MGZhZGYtOTc1MS00ZjczLThmNjUtODQ0Njc1YjlhMjJhL3ZlcmlmaWFibGVDcmVkZW50aWFscy9pc3N1ZSIsIm5vbmNlIjoid3h1UFl1NzI3QlJUYUtUNzdKWlQzUT09Iiwic3ViX2p3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJraWQiOiJkaWQ6d2ViOnZlcmlmaWVkLWlkLmZhY3RvcmxhYnMucGwjNWQzYjYxMjdiNjJlNGU4ODhjMmZjNmJlOTVlNzk4MjV2Y1NpZ25pbmdLZXktMmIwYjkiLCJrdHkiOiJFQyIsIngiOiJUV3dwNUE0M3oydmptbmRHOS1BR3NxWVU4bENMWkFwUWJPRmJFejRfcklFIiwieSI6Ik1wT0twb09VZnJJZExYeEFCbE9EMDNESTBTd3Zyc25xVXBOYjVQN1B4YWsifSwiZGlkIjoiZGlkOndlYjp2ZXJpZmllZC1pZC5mYWN0b3JsYWJzLnBsIiwiY2FyYm9ucHJpbnRuYW1lIjoiQURGWDo0OTozODU6MzE0OjI0IiwiY2FyYm9ucHJpbnR2YWx1ZSI6IjIwOCIsImlzcyI6Imh0dHBzOi8vc2VsZi1pc3N1ZWQubWUiLCJpYXQiOjE3MTUxMTQxNzIsImp0aSI6IjQzOTg0MDhhLTcyOGYtNGRjMy04ZGMxLTE0ZTY1MDJlYmNmNiIsImV4cCI6MTcxNTExNDQ3MiwicGluIjp7Imxlbmd0aCI6NCwidHlwZSI6Im51bWVyaWMiLCJhbGciOiJzaGEyNTYiLCJpdGVyYXRpb25zIjoxLCJzYWx0IjoiMWNkZTUxZTljOTU1NDFjZmJhNDg5YTFhNGJlZTU5YTYiLCJoYXNoIjoiZG0rTit3TExKbEdodmticUx5Z2VVNEY2NUova0MvWnA0L3ZjdXY4NDZvND0ifX0.Am0jUMyI-BzvxWjpnNPNebp_VQ44iuaod5DoNOLR8igG4uR0Brq4AtoAUUWgr-AB4qOhrM2fpc8ljT70__2h5A"
}
ID Token Hint Decoded:
{
"sub": "tvEsJA3LBChh4-sJLbBhpaM2tLEKYOlJW38b2I-yEHQ",
"aud": "https://beta.eu.did.msidentity.com/v1.0/tenants/6790fadf-9751-4f73-8f65-844675b9a22a/verifiableCredentials/issue",
"nonce": "wxuPYu727BRTaKT77JZT3Q==",
"sub_jwk": {
"crv": "secp256k1",
"kid": "did:web:verified-id.factorlabs.pl#5d3b6127b62e4e888c2fc6be95e79825vcSigningKey-2b0b9",
"kty": "EC",
"x": "TWwp5A43z2vjmndG9-AGsqYU8lCLZApQbOFbEz4_rIE",
"y": "MpOKpoOUfrIdLXxABlOD03DI0SwvrsnqUpNb5P7Pxak"
},
"did": "did:web:verified-id.factorlabs.pl",
"carbonprintname": "ADFX:49:385:314:24",
"carbonprintvalue": "208",
"iss": "https://self-issued.me",
"iat": 1715114172,
"jti": "4398408a-728f-4dc3-8dc1-14e6502ebcf6",
"exp": 1715114472,
"pin": {
"length": 4,
"type": "numeric",
"alg": "sha256",
"iterations": 1,
"salt": "1cde51e9c95541cfba489a1a4bee59a6",
"hash": "dm+N+wLLJlGhvkbqLygeU4F65J/kC/Zp4/vcuv846o4="
}
}
This demonstrates the clear connection between Verifiable Credentials and established OpenID Connect protocols.
Getting Started: Build Your Own Implementation
Build your own Wallet with Microsoft SDK or use Authenticator App. Authenticator Features:
- Secure Storage: Credentials stored locally on device
- Activity Logging: Complete audit trail of all credential activities
- Face Check: Biometric verification during presentation (when enabled)
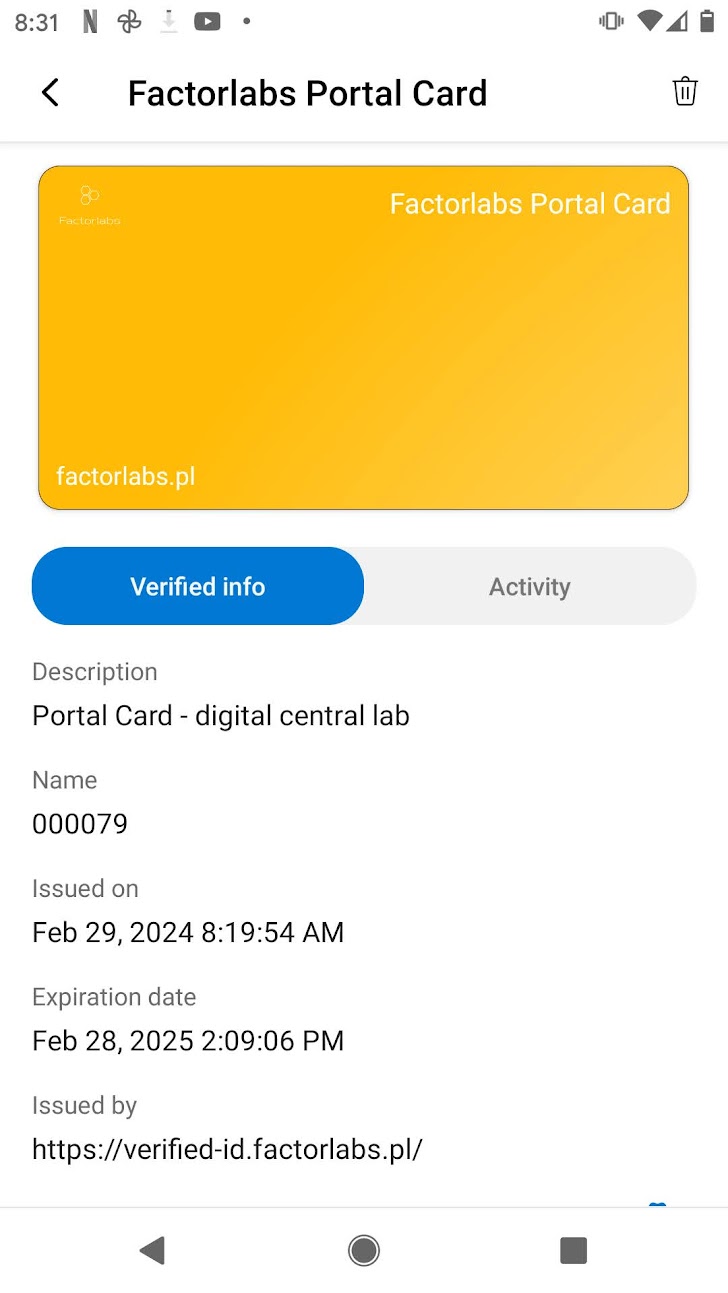
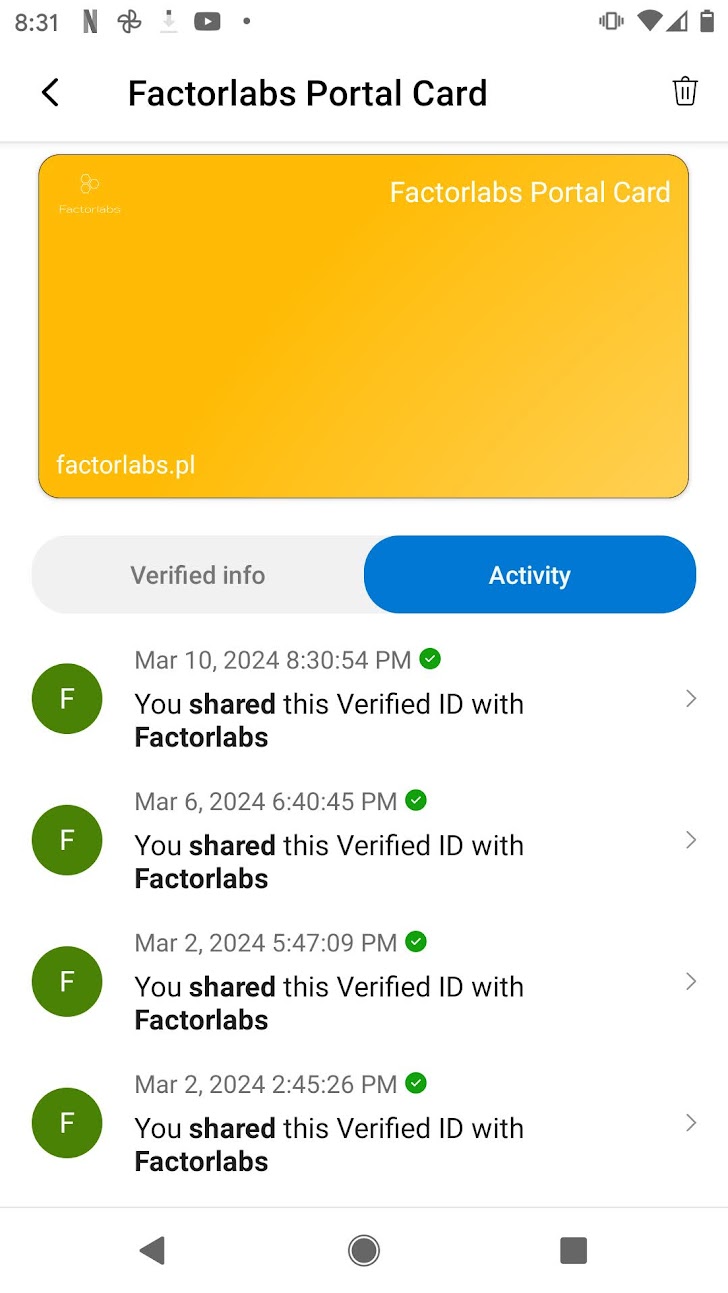
Face Check Process: Uses the photo stored in the credential claim (not your account photo) combined with Azure Cognitive Services for real-time facial verification during presentation.
On my own
GitHub Workshop: Start with my comprehensive workshop repository: Entra Verified ID Workshop
Sample Implementations:
Resources and Documentation
My Demo Pages
All demonstrations in one place: Demo Page
Microsoft Documentation
- Entra Verified ID Overview: Documentation
- Technical Setup Guide: Configuration
- Latest Features: What’s New
- Supported Standards: Standards Documentation
Industry Standards
- W3C Verifiable Credentials: Specification
- Payment Flows: Account-to-Account Draft
Summary and Next Steps
Future Opportunities: The technology foundation exists today for revolutionary applications in payments, supply chain verification, access control, and digital identity management. The question isn’t whether this will transform digital identity—it’s how quickly organizations will adopt these capabilities to create competitive advantages.
Ready to get started? Begin with the workshop and join the future of digital identity.
