TL;DR
It is not easy for Entra ID Tenant administrators to choose the best authentication method for their employees, vendors, and partners. You must consider the scenario, the environment, and the passwordless technology.
I’m focusing only the passwordless MFA authentication methods in the corresponding changes in the Entra ID - the MFA will be required.
Side note: Microsoft announced that MFA will be required for a couple of services, like Azure Portal or CLI. The document mentions that Security defaults will force MFA or should be enabled by Conditional Access Policies for users accessing the defined services. We will see how the final implementation will look like (I promise to update the post with the final state).
MFA
What is MFA - Multi-Factor Authentication? We will check it by definition and examples.
Definition
- Something you know.
- Something you have.
- Something you are.
Is username with password MFA authentication method? No, it is not. It is a single-factor authentication method. It is covered by the first point - something you know - username and password. So this is one factor/point from definition.
Is username, password, and OTP (one time password code - from code generator) Multi-Factor authentication? Yes, it is. The first point covers it - something you know - username and password and the second point - something you have - OTP from the code generator (you own the application/mobile device). These are two factors/points from the definition. Multi-factor authentication requires more than one factor.
Is Windows Hello for Business an MFA authentication method? Windows Hello for Business incorporates two of these factors: something you have (the user’s private key protected by the device’s security module) and something you know (your PIN).
Details
The start path for you can be a Microsoft document Concept Authentication Passwordless. You don’t need to click the link - based on the document I reused the table with the details about passwordless authentication methods:
| Persona | Scenario | Environment | Passwordless technology |
|---|---|---|---|
| Admin | Secure access to a device for management tasks | Assigned Windows 10 device | Windows Hello for Business and/or FIDO2 security key |
| Admin | Management tasks on non-Windows devices | Mobile or non Windows device | Passwordless sign-in with the Authenticator app |
| Information worker | Productivity work | Assigned Windows 10 device | Windows Hello for Business and/or FIDO2 security key |
| Information worker | Productivity work | Mobile or non Windows device | Passwordless sign-in with the Authenticator app |
| Frontline worker | Kiosks in a factory, plant, retail, or data entry | Shared Windows 10 devices | FIDO2 Security keys |
Based on the table above, I will describe the scenarios and the best options for the Entra ID.
Scenario 1
Company employee with a workstation (Windows 10 or newer) with company policies (Intune).

Best(easies to use) option: Windows Hello for Business
Details
- One employee with one assigned (dedicated) device/workstation.
- Windows Hello for Business is required.
Pros
- Windows Hello for Business is a secure and easy-to-use passwordless method.
- Access is easy - just a fingerprint or face recognition.
Cons
- Single tenant connection.
- The company device is connected (enrolled) with the Entra ID (Intune required).
Scenario 2:
Support - external partner with access to Entra ID. We are support company - our duty is to support other companies to maintain their Entra ID. Per each contract, we have access to the customer Entra ID. We can’t be locked to the OS and device.
Scenario 2.1:
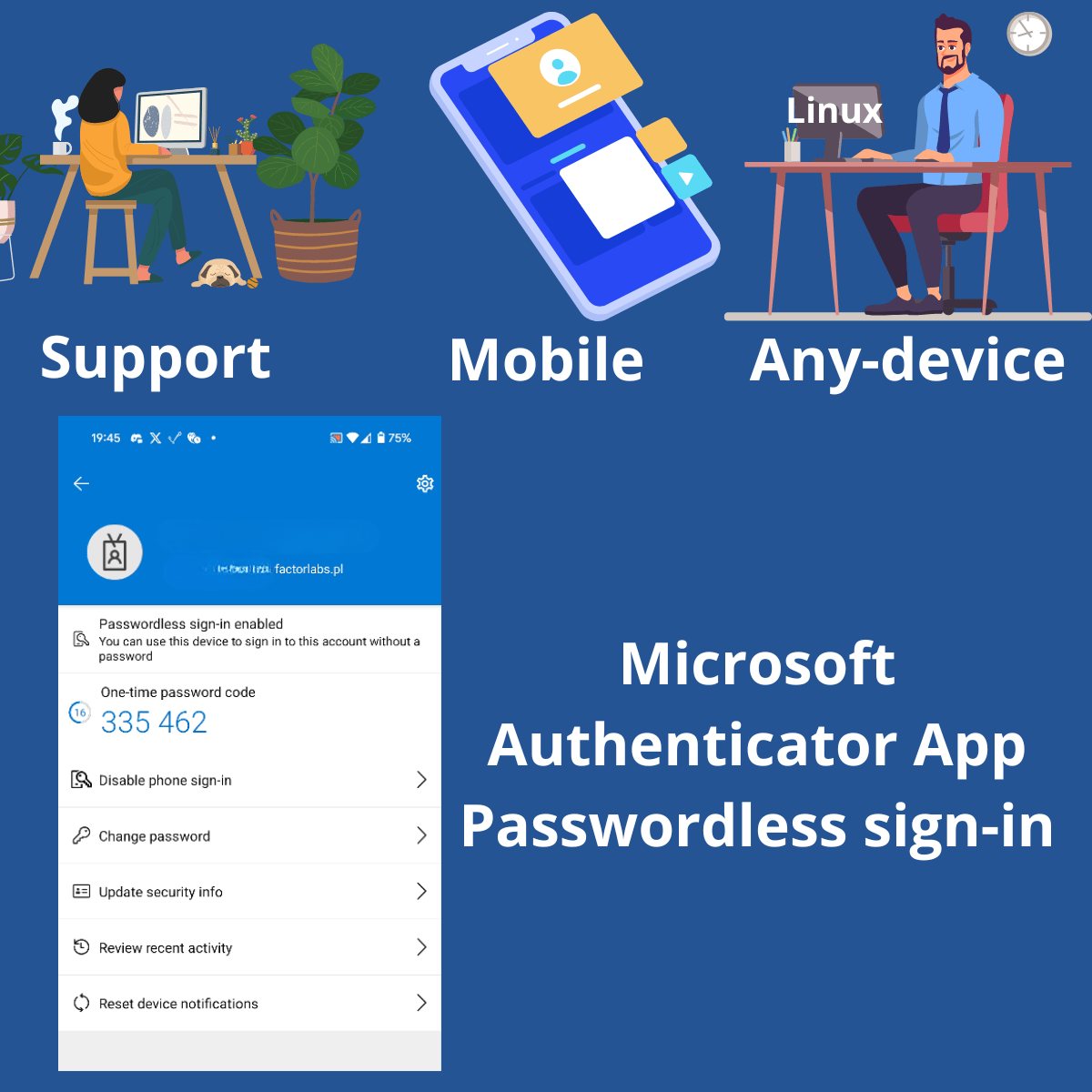
First option: Passwordless sign-in with the Authenticator App.
Details
- Windows Hello for Business is not an option - we don’t have an enrolled device.
- We want to authenticate from any device, not only desktop but mobile.
Pros
- passwordless
- Authentication from any device and service: mobile application, web application, desktop application, CLI/Console application on any OS, etc.
- My mobile phone is always with me, and I can authenticate anywhere.
Cons
- It is more complicated to use than via
Hello for Business. Open the browser, then take the phone, open the app, authenticate, click the notification, fill in the number, and click to log in. - A mobile device is required for the Microsoft Authenticator App.
Scenario 2.2
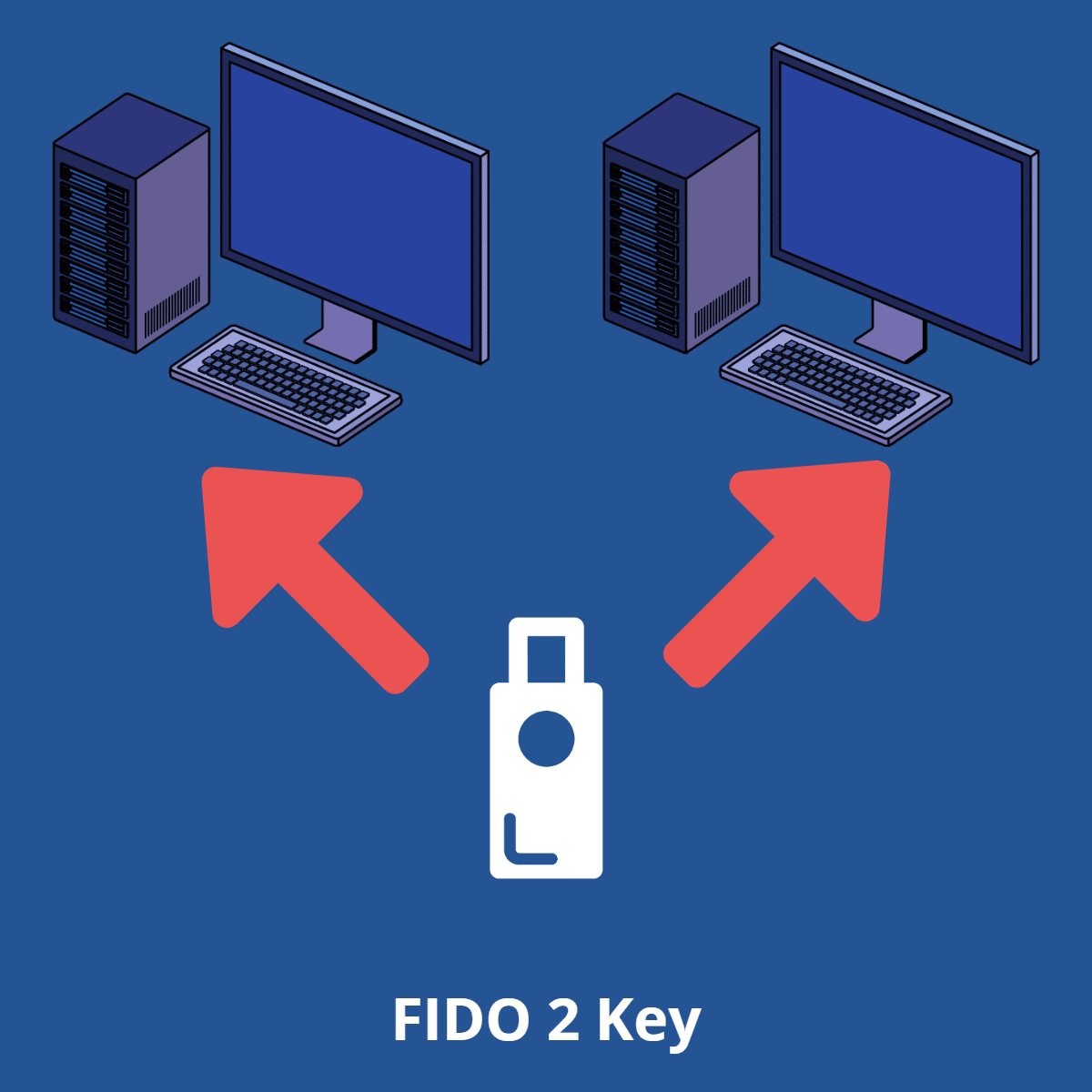
Second option: FIDO2 security key
Details
With the FIDO2 security key, you can access Entra ID from any device (mobile, non-Windows device) via key, not via the Authenticator app.
Pros
- PIN & Click - easy to use.
- You can store many credentials.
- Also, best option for Brake Glass accounts.
Cons
- More complex to use than Windows Hello for Business.
- FIDO2 key required.
- A limited number of logins (accounts) on the device.
Summary
There is no simple way to decide on the authentication method. It would be best if you considered the expected scenario. Daily, the best option is Windows Hello for Business: this is the easiest way to authenticate. But also, when you need to log in from a different from your Windows workstation, you can use the Authenticator app or FIDO2 key. So, there is no way to use one authentication method, and there is no authentication method that solves all the problems.
Based on the scenarios and Microsoft recommendations, setting up both authentication methods, Windows Hello for Business and passwordless sign-in with the Authenticator app, will fit most 99% of cases.
Links
- https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/#windows-hello-and-two-factor-authentication
- https://learn.microsoft.com/en-us/entra/identity/authentication/howto-authentication-passwordless-deployment
- https://learn.microsoft.com/en-us/entra/identity/authentication/concept-authentication-passwordless#choose-a-passwordless-method
- YT video - experience with passwordless - Windows Hello for Business (from 4:20): https://youtu.be/5LJIv4-034E?t=260
- https://learn.microsoft.com/en-us/entra/identity/authentication/concept-mandatory-multifactor-authentication#prepare-for-multifactor-authentication and blog post https://azure.microsoft.com/en-us/blog/announcing-mandatory-multi-factor-authentication-for-azure-sign-in/
- https://learn.microsoft.com/en-us/entra/identity/role-based-access-control/security-emergency-access