
B2B scenario
Protect your applications and services with identity provider service based on the OpenID Connect with Identity Federations. Your solution is a ‘family’ of services and applications in the B2B model. Your partners have their identity provider—modern services like Entra ID, Octa, Auth0, and AWS Cognito.
Use cases
There will be no more duplicate accounts. You can use the partner identity to authenticate with our services. The email is a unique identifier, along with the password or another authentication method you provide as a partner. We hope that you can secure your accounts. When we see a risk, we can enable MFA for the B2B partner users.
Onboarding for new users from partners should be as easy as possible. For the end user, it is simple: fill in the email address or click the company logo—that’s it.
Onboarding for Partners will require setting up OpenID Connect Federation. No custom logic and frameworks are needed.
As a ‘B2B service’ owner, you can limit features and points of failure. Password resets and account lockouts will be eliminated from your system. An admin portal to manage users will be part of the partner solution (identity provider), so no custom portal from the service is needed.
Overview of the solution
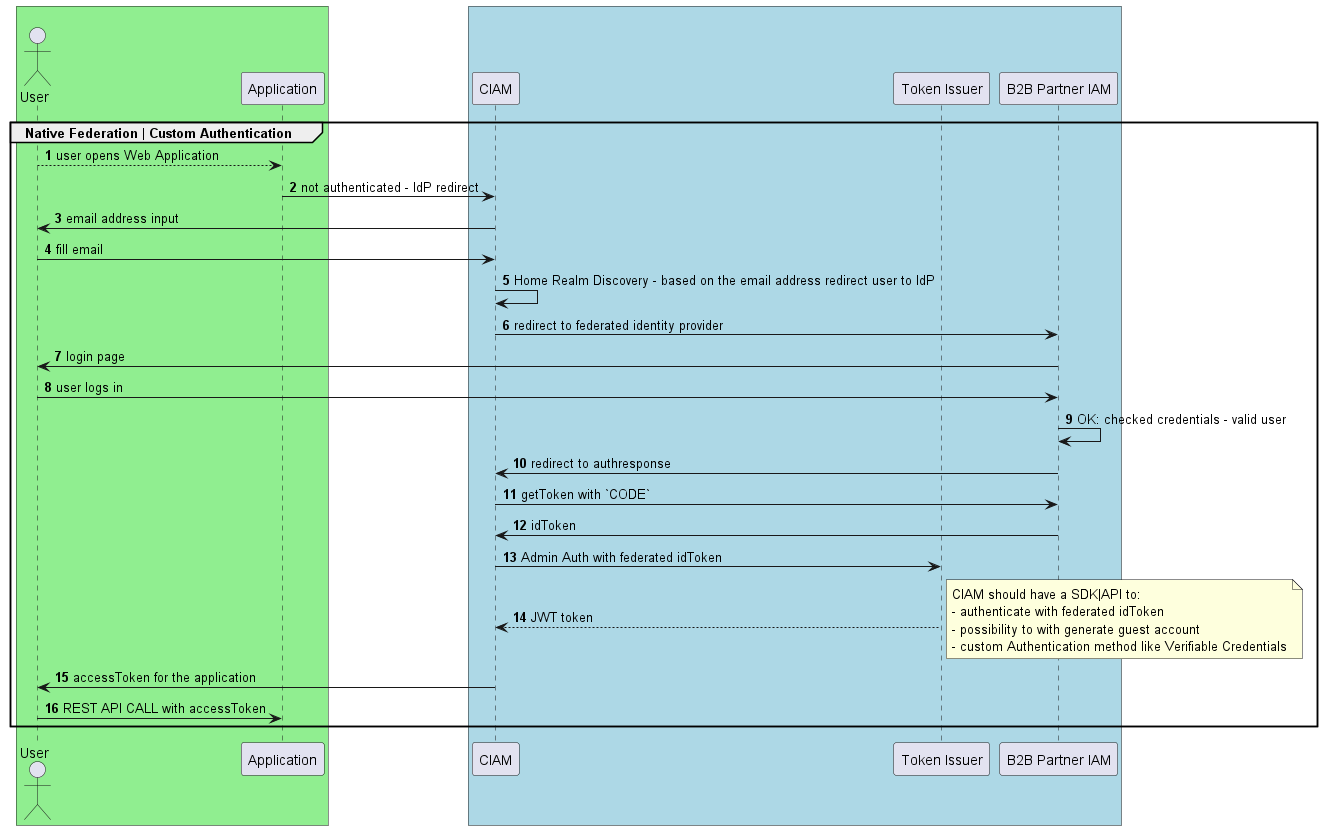
Technical details
Based on OpenID Connect and identity federation with partners, we decided to use JWT, an Access token issued by our identity provider service, to protect our services.
The easiest way to do this is to build flow like in the picture below:
- user is authenticated via the partner identity provider (federation)
- all accounts are protected with the expected security level by the organisation (MFA, Conditional Access, FIDO2, etc.)
- based on the organisation idToken with the Admin API/SDK we can issue|generate the expected JWT tokens for the user
Requirements/limitations:
- The described flow is based on the OpenID Connect.
- The Web Browser (Chrome, Firefox, Safari) is needed to authenticate the user.
- The partner identity provider secures accounts,
- No additional MFA is required. If needed, the process should be extended as a multi-step process.
Supported platforms to build the solution:
Cognito
Using the AWS Cognito Service, you can implement the federation logic using GetOpenIdTokenForDeveloperIdentity with your backend service, as indicated by point number 13 on the diagram.
The link to the Cognto documentation.