Microsoft Entra ID External Identities vs Azure AD B2C.
TL;DR
A summary of differences between Entra ID and Azure AD B2C. Entra ID in this article is used to build a product.
Differences between Entra ID and Azure AD B2C
To share resources from your organization (Entra ID) like PowerBi, OneDrive, and SharePoint - use B2B collaboration. Please remember: in many cases, you must assign the expected licenses - PowerBI*, for example, and you will be able to use PowerBI Portal.
This solution is also possible when you want to build a product based on PowerBI or OneDrive - In that case, you should consider setting up a dedicated ‘product’ tenant - to separate access to the resources.
The best option for a custom-developed application (SaaS) is Azure AD B2C. You can federate with many identity providers like Entra ID, Facebook, and Google.
| service name | B2B Collaboration | Azure AD B2C |
|---|---|---|
| PowerBI | Yes * | No |
| OneDrive | Yes * | No |
- There are some limitations to accessing resources in Microsoft Entra ID B2B collaboration.
Sample scenario diagram
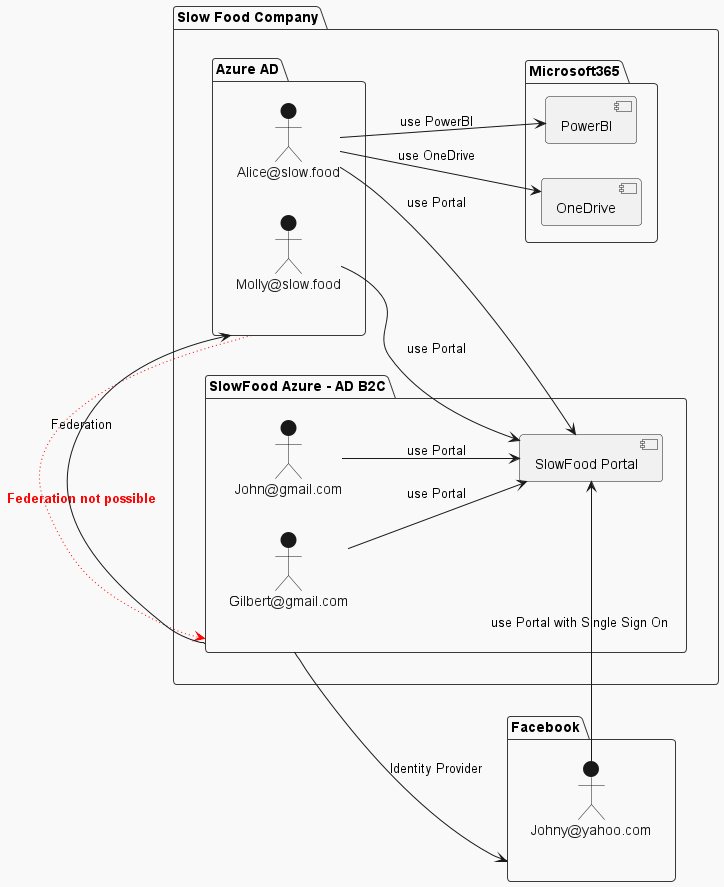
Table with details of the scenario
| User | Description | SlowFood Portal | SlowFood OneDrive * | SlowFood PowerBi * |
|---|---|---|---|---|
| [email protected] | Facebook user | yes, SSO via Facebook federation | no | no |
| [email protected] | Entra ID user | yes, SSO via federation | yes, SSO | yes, SSO |
| [email protected] | Entra ID user | yes, SSO via federation | yes, SSO | yes, SSO |
| [email protected] | Azure AD B2C user | yes, password in Azure AD B2C | no | no |
| [email protected] | Azure AD B2C user | yes, password in Azure AD B2C | no | no |
- The access to OneDrive/PowerBI is expected as standard Microsoft Entra ID (from the organization) user, not direct one-time access to file/report.
Future
Microsoft is working on the new feature - Microsoft Entra External ID. Maybe they will extend possibilities with B2B collaboration from the new CIAM tenant type. Will see….
Also, instead of working with Custom Policies (XML), there will be a user journey with API support. For example, you can call API to enrich the token with additional claims.
Additional cases
Also, to access the Microsoft 365 resources, you can use Service Principal access. So, without direct user access and permissions, you can share/connect Sharepoint to share the data. It is a good option for a custom-developed application (SaaS) that can use only Azure AD B2C (or Entra External ID in the future) and with the backend service (API) to access the data via the service principal.
Documentation & Links
- Set up sign-in for multi-tenant Azure Active Directory using custom policies in Azure Active Directory B2C
- Set up sign-up and sign-in with a Facebook account using Azure Active Directory B2C
- External Identities in Azure Active Directory, Comparing External Identities feature sets
- Microsoft Entra External ID
- Microsoft Entra External ID - Technical Documentation