Tl;dr
Security and privacy are paramount in today’s digital age, especially regarding personal information and interactions. One innovative approach to bolstering security in digital communications, such as phone calls, is using verifiable credentials for authentication.
Details
Here’s a simplified explanation of how phone call authentication via verifiable credentials works. Imagine you receive a phone call from a service provider, say your customer. Instead of going through the traditional and often tedious method of answering security questions (which could be guessed or obtained by someone else), the authentication process involves a digital handshake using verifiable credentials.
Process
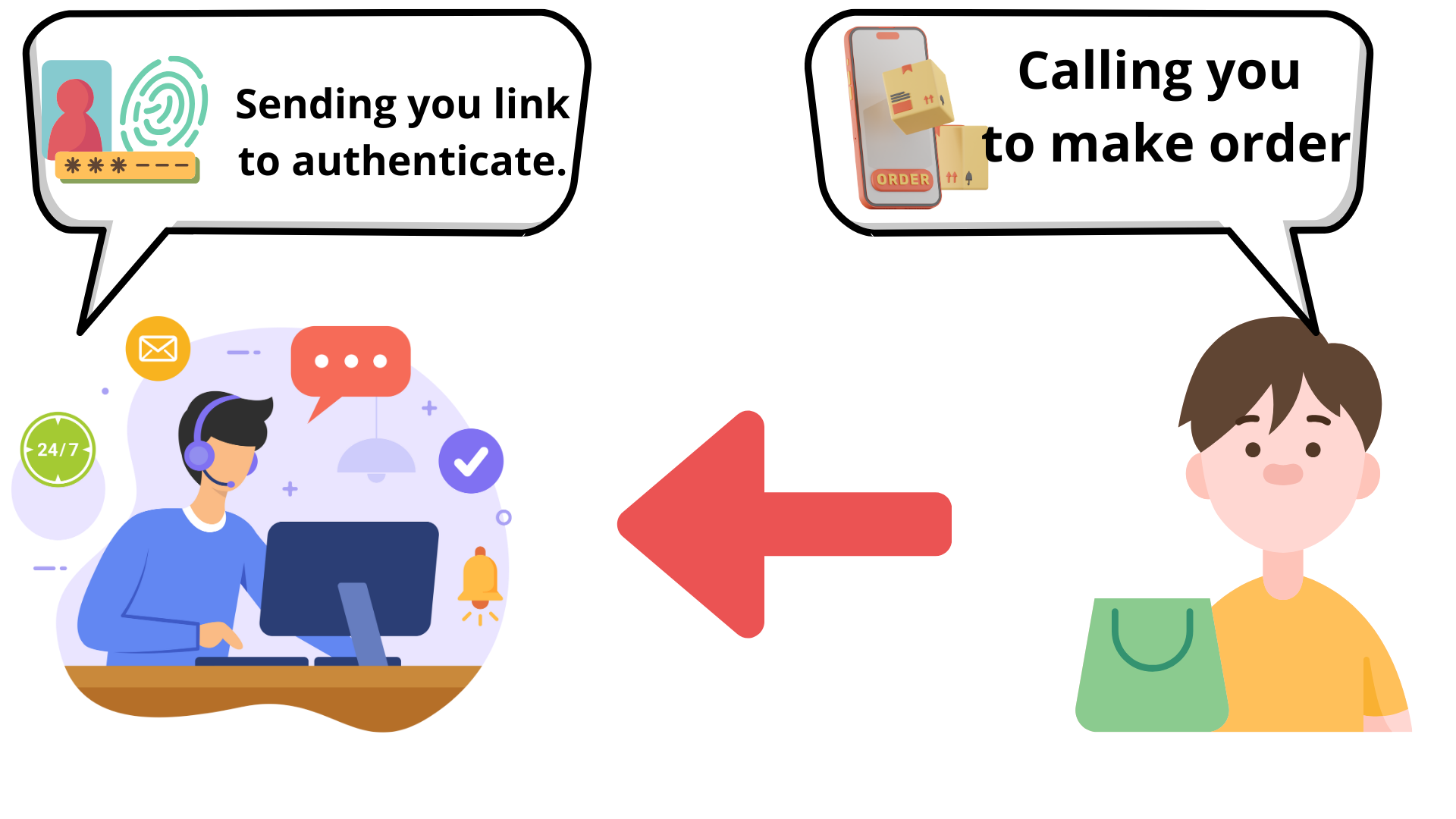
Verifiable credentials are digital certificates, similar to digital IDs, that prove the identity of the caller and the call recipient. These credentials can be stored securely in a digital wallet on your smartphone or another device. When a customer initiates a call, the operator requests authentication with the link - to share|present credential (VC). This process is facilitated by cryptographic methods, ensuring that the credentials are authentic and have not been tampered with. We can compare the case to the physical ID card, where the issuer is the government, and the owner is the person who has the ID card. By the office window, the owner shows the ID card, and the office checks the data and security marks on the card. However, the office can also verify the digital layer of the card.
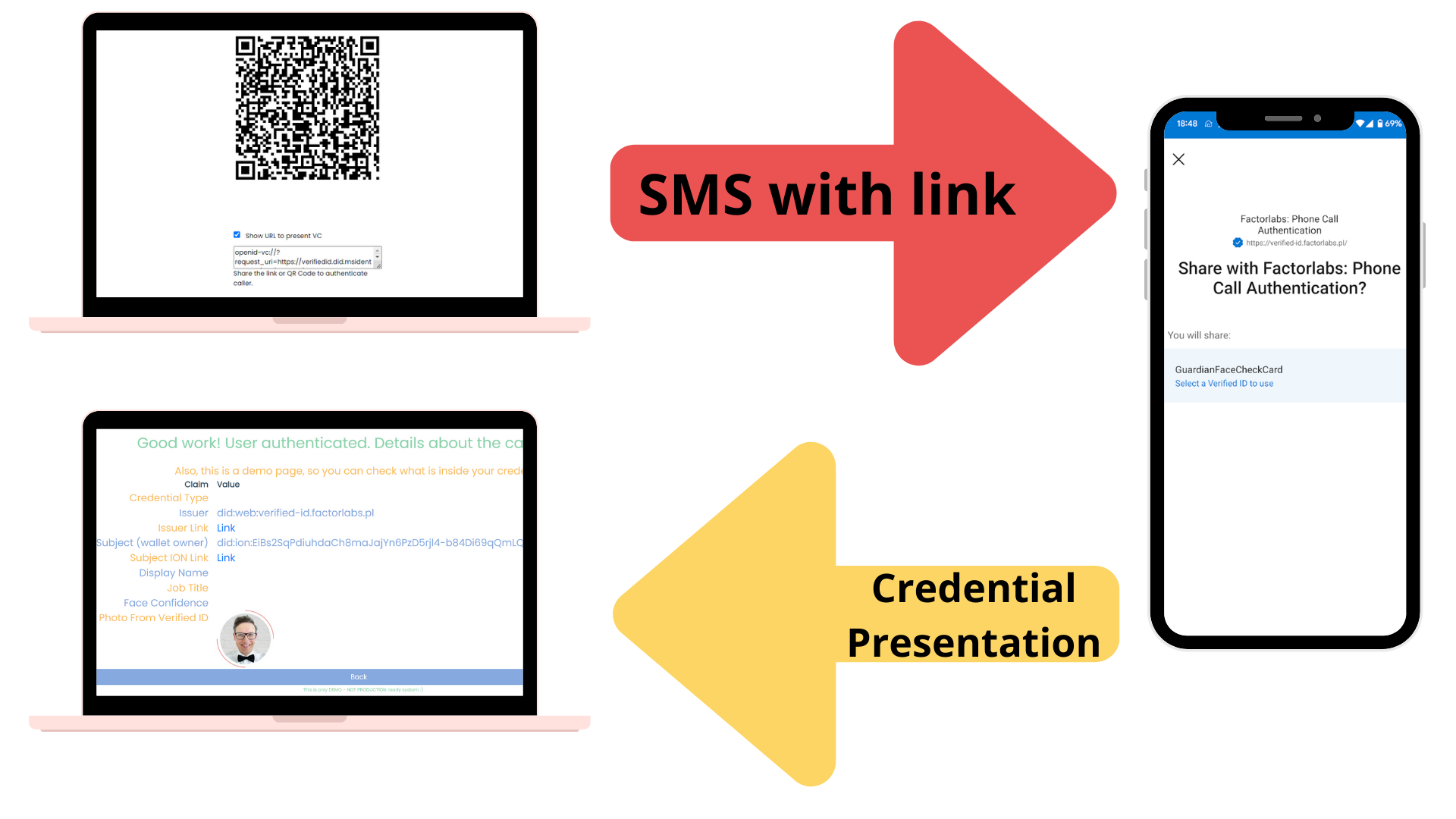 You can test the full flow with my demo application. All steps:
You can test the full flow with my demo application. All steps:
- The account onboarding process should include the step to issue the Verifiable Credential - you can try with my demopage.
- As a Phone Call Recipient, the phone call operator will verify the caller with the page.
- The operator gets the link generated to share VC. You can copy the link and share it with the caller via text. The caller can use the link to verify the call.
- The caller will use the link to open the wallet and share expected data (Verifiable Credentials) with the recipient.
- The recipient will receive the data and verify the call.
Technical details & services
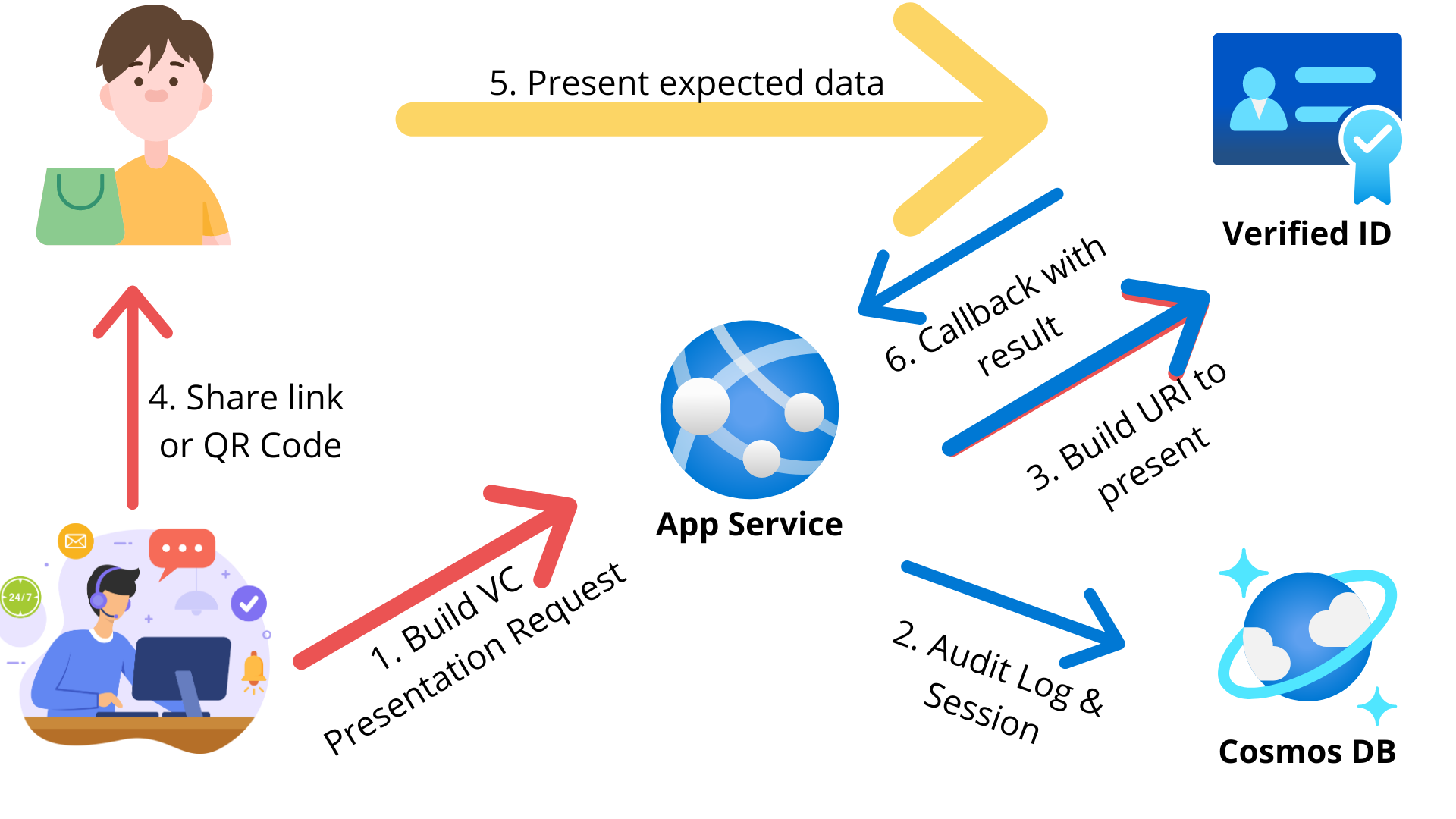
To build the service and the demo, I used the following services:
- App Service.
- Cosmos DB (to store audit log & session).
- Entra Verified ID (to issue and verify the credentials).
What next?
 I see the next possibilities for similar business cases:
I see the next possibilities for similar business cases:
- Security check on the office|factory entrance.
- For internal organizational cases, Verified Employee credentials can be used (build-in credentials).
- A similar process can be used to verify that the bank employee is calling the customer to be 100% sure that the bank employee is calling.
- Face Check can extend the process to improve security.
- Extend the process with the KYC (Know Your Customer) process - the onboarding process can verify the customer’s physical ID, selfie, and other data.
- Full audit trail - from the verification and presenter sides.